D-Link DGS-6600-48TS Configuration Guide - Page 466
Configuring an allow-untrusted port, Configuring Snooping Trusts
 |
View all D-Link DGS-6600-48TS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 466 highlights
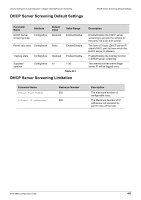
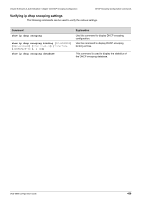
Volume 8-Security & Authentication / Chapter 44-DHCP Snooping Configuration DHCP Snooping Configuration Commands Configuring an "allow-untrusted port" The DHCP snooping function validates the DHCP packets when it arrives at the port on the VLAN that is enabled for DHCP snooping. By default, the validation process will drop the packet If gateway address!=0 or option 82 is present. Use the ip dhcp snooping information option allow-untrusted command to allow the packet with relay option 82 arriving at the un-trusted interface. Command ip dhcp snooping information option allowuntrusted Explanation Use this command to globally allow DHCP packets with relay option 82 on the un-trusted interface. Use the no form of the command to not allow the packets with relay option 82. This example shows how to enable DHCP snooping option-82 allow-untrusted port: DGS-6600# configure terminal DGS-6600(config)# ip dhcp snooping information option allow-untrusted DGS-6600(config)# Configuring Snooping Trusts Normally, the ports connected to DHCP server or to other switches should be configured as a trusted interface. The ports connected to DHCP clients should be configured as un-trusted interface. When a port is configured as an un-trusted interface, the DHCP message arrives at the port on a vlan that is enabled for DHCP and snooping will be validated by the following checks. (1)The received message should be all sent by the client. If the message is sent by the DHCP server, the message will be dropped. (2)If ip dhcp snooping verify mac-address is enabled, the source MAC in the Ethernet header must be the same as the DHCP client hardware address to pass the validation. (3)For the received release and decline packets, the received port is also checked against the binding database entry. The packet will be dropped if inconsistent. (4)If gateway address!=0 or option 82 is present, the packet is dropped In addition to doing the validation, DHCP snooping also create a binding entry based on the IP address assigned to client by the server in DHCP snooping binding database. The binding entry contains information including MAC address, IP address, the VLAN ID and port ID where the client is located, and the expiry of the lease time. Command ip dhcp snooping trust Explanation Use this command to configure a port as interface trusted for DHCP snooping. Use the no form of this command to return to the default setting. This example shows how to enable DHCP snooping trust for port 3.3: DGS-6600(config)# interface eth3.3 DGS-6600(config-if)# ip dhcp snooping trust DGS-6600(config)# DGS-6600 Configuration Guide 466