Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 100
Local DB, SQL DB, Active Directory, LDAP Directory or Token Servers with a RADIUS interface.
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 100 highlights
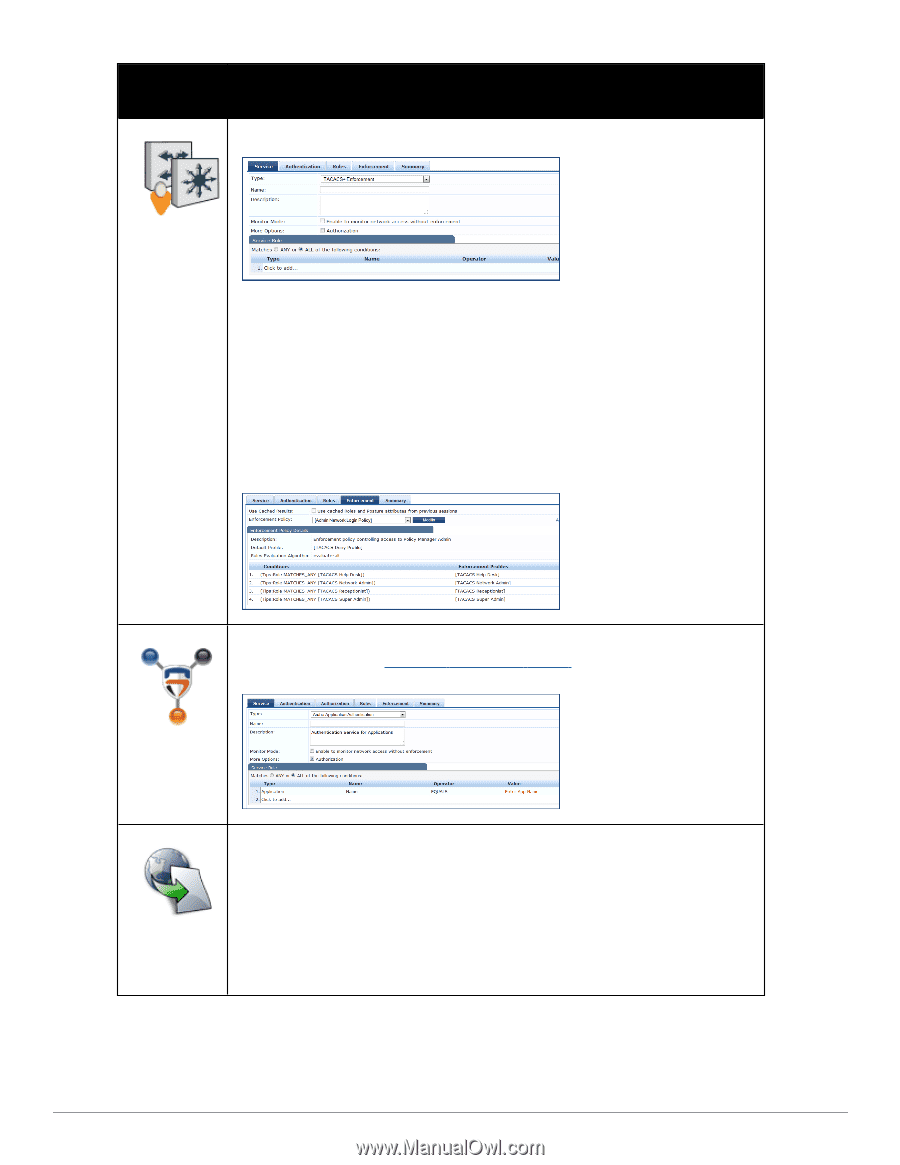
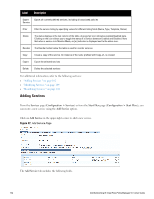
Service Type Description/ Available Policy Components (in tabs)/ Service Rule (in Rules Editor)/ Service-specific policy components (called out with legend below) Template for any kind of TACACS+ request. TACACS+ Enforcement NOTE: No default rule is associated with this service type. Rules can be added to filter the request based on the Date and Connection namespaces. See "Rules Editing and Namespaces" on page 341 for more information. TACACS+ users can be authenticated against any of the supported authentication source types: Local DB, SQL DB, Active Directory, LDAP Directory or Token Servers with a RADIUS interface. Similarly, service level authorization sources can be specified from the Authorization tab. Note that this tab is not enabled by default. Select the Authorization check box on the Service tab to enable this feature. A role mapping policy can be associated with this service from the Roles tab. The result of evaluating a TACACS+ enforcement policy is one or more TACACS+ enforcement profiles. For more information on TACACS+ enforcement profiles, see "TACACS+ Enforcement Profiles " on page 224 for more information. This type of service provides authentication and authorization to users of Dell applications: GuestConnect and Insight. Application Enforcement Profiles can be sent to these or other generic applications for authorizing the users. DellW-Series Application Authentication Web-based authentication service for guests or agentless hosts. The Cisco switch hosts a captive portal; the portal web page collects username and password. The switch then sends a RADIUS request in the form of a PAP authentication request to Policy Manager. Cisco WebAuthentication Proxy 100 Dell Networking W-ClearPass Policy Manager 6.0 | User Guide