Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 49
Policy Manager Policy Model, Services Paradigm
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 49 highlights
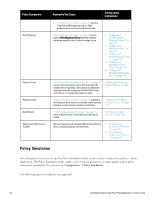
Chapter 5 Policy Manager Policy Model From the point of view of network devices or other entities that need authentication and authorization services, Policy Manager appears as a RADIUS, TACACS+ or HTTP/S based Authentication server; however, its rich and extensible policy model allows it to broker security functions across a range of existing network infrastructure, identity stores, health/posture services and client technologies within the Enterprise. Refer to the following topics for additional information. l "Services Paradigm" on page 49 n "Viewing Existing Services " on page 52 n "Adding and Removing Services " on page 52 n "Links to Use Cases and Configuration Instructions " on page 53 l "Policy Simulation" on page 54 n "Add Simulation Test" on page 56 n "Import and Exporting Simulations " on page 59 Services Paradigm Services are the highest level element in the Policy Manager policy model. They have two purposes: l Unique Categorization Rules (per Service) enable Policy Manager to test Access Requests ("Requests") against available Services to provide robust differentiation of requests by access method, location, or other network vendor-specific attributes. NOTE: Policy Manager ships configured with a number of basic Service types. You can flesh out these Service types, copy them for use as templates, import other Service types from another implementation (from which you have previously exported them), or develop new Services from scratch l By wrapping a specific set of Policy Components, a Service can coordinate the flow of a request, from authentication, to role and health evaluation, to determination of enforcement parameters for network access. The following image illustrates and describe the basic Policy Manager flow of control and its underlying architecture. Dell Networking W-ClearPass Policy Manager 6.0 | User Guide 49