Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 109
Authentication and Authorization, Architecture and Flow
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 109 highlights
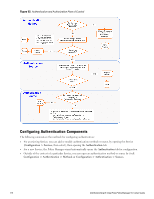
Chapter 13 Authentication and Authorization As the first step in Service-based processing, Policy Manager uses an Authentication Method to authenticate the user or device against an Authentication Source. Once the user or device is authenticated, Policy Manager fetches attributes for role mapping policies from the Authorization Sources associated with this Authentication Source. Architecture and Flow Policy Manager divides the architecture of authentication and authorization into three components: l Authentication Method. Policy Manager initiates the authentication handshake by sending available methods, in priority order, until the client accepts a methods or until it NAKs the last method, with the following possible outcomes: n Successful negotiation returns a method, for use in authenticating the client against the Authentication Source. n Where no method is specified (for example, for unmanageable devices), Policy Manager passes the request to the next configured policy component for this Service. n Policy Manager rejects the connection. NOTE: An Authentication Method is only configurable for some service types (Refer to "Policy Manager Service Types" on page 92). All 802.1X services (wired and wireless) have an associated Authentication Method. An authentication method (of type MAC_AUTH) can be associated with MAC authentication service type. l Authentication Source. In Policy Manager, an authentication source is the identity store (Active Directory, LDAP directory, SQL DB, token server) against which users and devices are authenticated. Policy Manager first tests whether the connecting entity - device or user - is present in the ordered list of configured Authentication Sources. Policy Manager looks for the device or user by executing the first Filter associated with the authentication source. Once the device or user is found, Policy Manager then authenticates this entity against this authentication source. The flow is outlined below: n On successful authentication, Policy Manager moves on to the next stage of policy evaluation, which is to collect role mapping attributes from the authorization sources. n Where no authentication source is specified (for example, for unmanageable devices), Policy Manager passes the request to the next configured policy component for this Service. n If Policy Manager does not find the connecting entity in any of the configured authentication sources, it rejects the request. n Once Policy Manager successfully authenticates the user or device against an authentication source, it retrieves role mapping attributes from each of the authorization sources configured for that authentication source. It also, optionally, can retrieve attributes from authorization sources configured for the Service. The flow of control for authentication takes these components in sequence: Dell Networking W-ClearPass Policy Manager 6.0 | User Guide 109