Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 128
Services, Configuration > Service, Add Service, Configuration >, Authentication > Sources
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 128 highlights
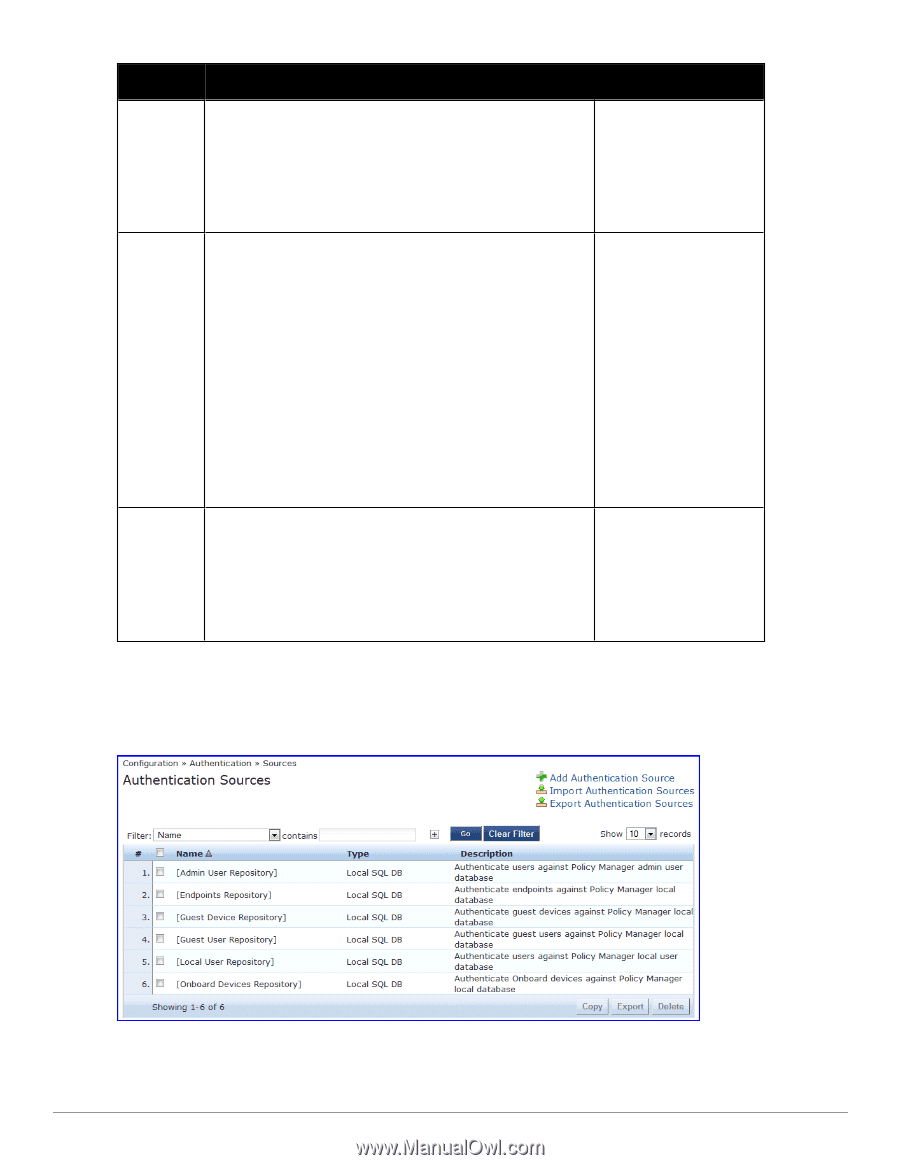
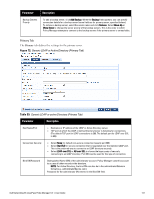
Source Description Special Considerations Policy Manager can also use the RADIUS attributes returned from a token server to create role mapping policies. See "Namespaces" on page 341. Internal User Database HTTP An internal relational database stores Policy Manager configuration data and locally configured user and device accounts. Three pre-defined authentication sources, [Local User Repository] , [Guest User Repository], and [Guest Device Repository], represent the three databases used to store local users, guest users and registered devices, respectively. While regular users typically reside in an authentication source such as Active Directory (or in other LDAP-compliant stores), temporary users, including guest users can be configured in the Policy Manager local repositories. For a user account created in the local database, the role is statically assigned to that account, which means a role mapping policy need not be specified for user accounts in the local database. However, if new custom attributes are assigned to a user (local or guest) account in the local database, these can be used in role mapping policies. The local user database is pre-configured with a filter to retrieve the password and the expiry time for the account. Policy Manager can perform MSCHAPv2 and PAP/GTC authentication against the local database. The HTTP authentication source relies on the GET method to retrieve information. The client submits a request, and then the server returns a response. All request parameters are included in the URL. For example: URL: https//hostname/webservice/.../%{Auth:Username}?param1=% {...}¶m2=value2 HTTP relies on the assumption that the connection between the client and server computers is secure and can be trusted. From the Services page (Configuration > Service), you can configure authentication source for a new service (as part of the flow of the Add Service wizard), or modify an existing authentication source directly (Configuration > Authentication > Sources, then click on its name in the listing page). Figure 69: Authentication Sources Listing Page 128 Dell Networking W-ClearPass Policy Manager 6.0 | User Guide