Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 240
Additional Available Tasks, Adding and Modifying Proxy Targets, Configuration > Network > Proxy
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 240 highlights
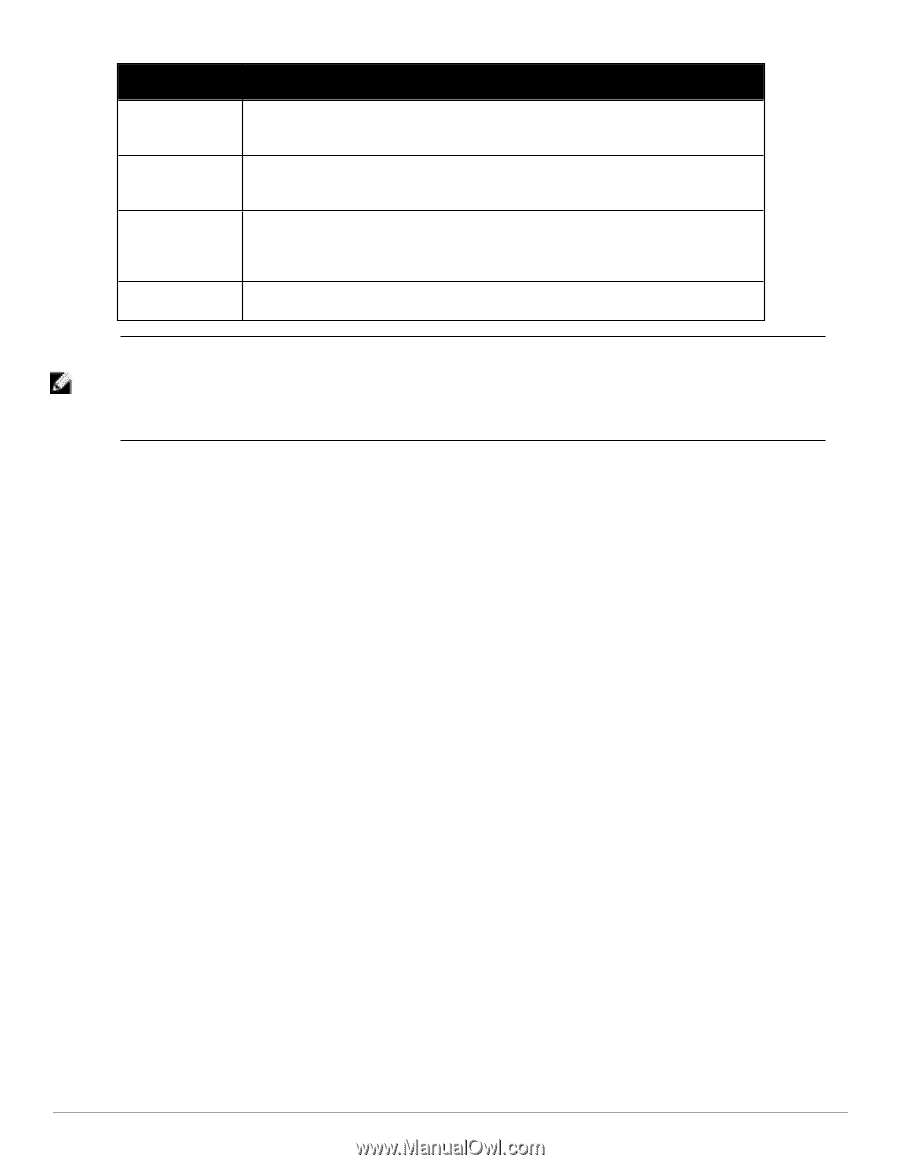
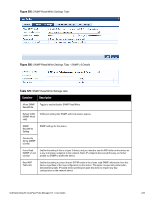
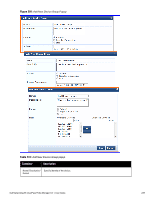
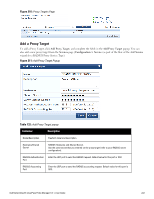
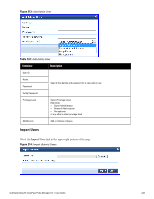
Container Description Subnet Enter a subnet consisting of network address and the network suffix (CIDR notation); for example, 192.168.5.0/24 Regular Expression Specify a regular expression that represents all IPv4 addresses matching that expression; for example, ^192(.[0-9]*){3}$ List: Available/Selected Devices Use the widgets to move device identifiers between Available and Selected. Click Filter to filter the list based on the text in the associated text box. Save/Cancel Click Save to commit or Cancel to dismiss the popup. NOTE: For SNMP enforcement on the network device, one or more of the following traps have to be configured on the device: Link Up trap, Link Down trap, MAC Notification trap. In addition, one or more of the following SNMP MIBs must be supported by the device: RFC-1213 MIB, IF-MIB, BRIDGE-MIB, ENTITY-MIB, Q-BRIDGE-MIB, CISCO-VLAN-MEMBERSHIP-MIB, CISCO-STACK-MIB, CISCO-MAC-NOTIFICATION-MIB. These traps and MIBs enable Policy Manager to correlate the MAC address, IP address, switch port, and switch information. Additional Available Tasks l To import a Device Group, click Import Device Groups; in the Import from File popup, browse to select a file, then click Import. l To export all Device Groups from the configuration, click Export Devices; in the Export to File popup, specify a file path, then click Export. l To export a single Device Group from the configuration, select it (using the check box on the left), then click Export; in the Save As popup, specify a file path, then click Export. l To delete a single Device Group from the configuration, select it (using the check box on the left), then click Delete; commit the deletion by selecting Yes. dismiss the popup by selecting No. Adding and Modifying Proxy Targets In Policy Manager, a proxy target represents a RADIUS server (Policy Manager or third party) that is the target of a proxied RADIUS request. For example, when a branch office employee visits a main office and logs into the network, Policy Manager assigns the request to the first Service in priority order that contains a Service Rule for RADIUS proxy Services and appending the domain to the Username. Proxy targets are configured at a global level. They can then used in configuring RADIUS proxy Services. (Refer to "Policy Manager Service Types" on page 92.) Policy Manager lists all configured proxy servers in the Proxy Servers page: Configuration > Network > Proxy Servers. 240 Dell Networking W-ClearPass Policy Manager 6.0 | User Guide