Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 54
Policy Simulation, Configuration > Policy Simulation
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 54 highlights
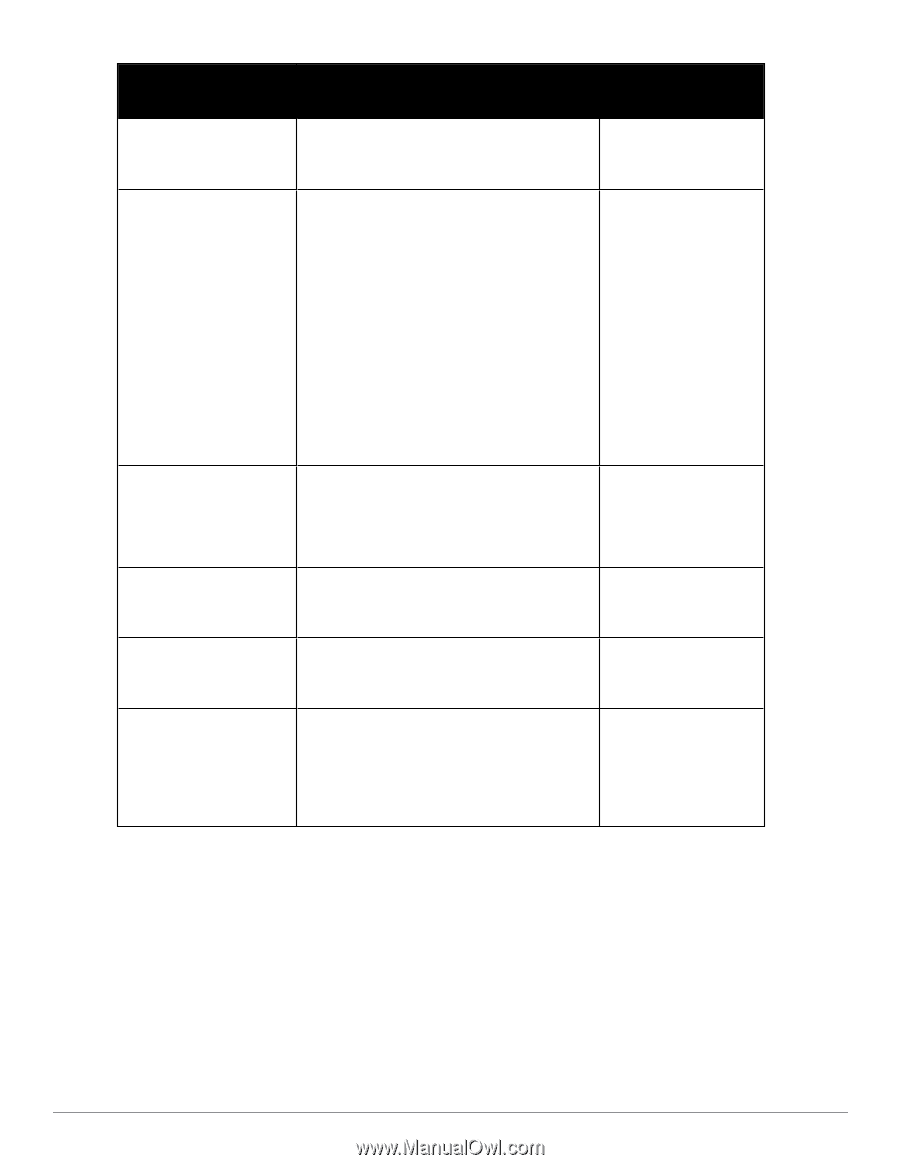
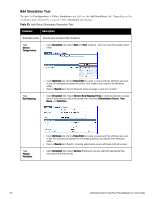
Policy Component Role Mapping Posture Policy Posture Server Audit Server Enforcement Policy and Profiles Illustrative Use Cases Configuration Instructions l "TACACS+ Use Case" on page 83 uses the local Policy Manager repository. Other authentication sources would also be fine. "802.1x Wireless Use Case" on page 67 has an explicit Role Mapping Policy that tests request attributes against a set of rules to assign a role. l "Adding and Modifying Role Mapping Policies " on page 155 l "Adding and Modifying Roles " on page 158 l "Adding and Modifying Local Users " on page 159 l "Adding and Modifying Guest Users " on page 161 l "Adding and Modifying Static Host Lists " on page 166 "Web Based Authentication Use Case " on page 73 uses an internal posture policy that evaluates the health of the originating client, based on attributes submitted with the request by the Dell Web Portal, and returns a corresponding posture token. "Adding and Modifying Posture Policies " on page 172 "802.1x Wireless Use Case" on page 67 appends a third-party posture server to evaluate health policies based on vendor-specific posture credentials. "Adding and Modifying Posture Servers " on page 199 " MAC Authentication Use Case " on page 79, uses an Audit Server to provide port scanning for health. "Configuring Audit Servers" on page 204 All Use Cases have an assigned Enforcement Policy and corresponding Enforcement Rules. l "Configuring Enforcement Profiles " on page 218 l "Configuring Enforcement Policies " on page 229 Policy Simulation Once the policies have been set up, the Policy Simulation utility can be used to evaluate these policies - before deployment. The Policy Simulation utility applies a set of request parameters as input against a given policy component and displays the outcome, at: Configuration > Policy Simulation. The following types of simulations are supported: 54 Dell Networking W-ClearPass Policy Manager 6.0 | User Guide