Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 137
Table 64, Filter Creation Steps
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 137 highlights
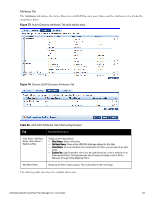
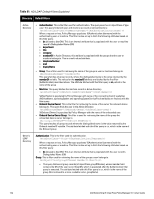
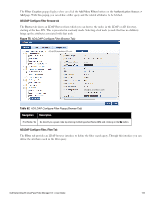
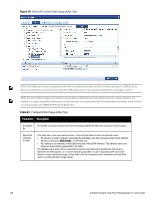
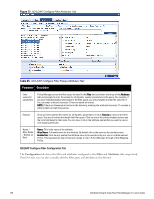
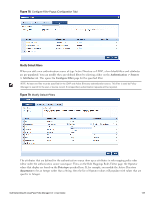
Parameter Description The following tables describes the steps used in creating a filter. Table 64: Filter Creation Steps Step Description Step 1 Select filter node The goal of filter creation is to help Policy Manager understand how to find a user or device connecting to the network in LDAP or Active Directory. From the Filter tab, click on a node that you want to extract user or device information from. For example, browse to the Users container in Active Directory and select the node for a user (Alice, for example). On the right hand side, you see attributes associated with that user. Step 2 Select attribute Click on attributes that will help Policy Manager to uniquely identify the user or device. For example, in Active Directory, an attribute called sAMAccountName stores the user ID. The attributes that you select are automatically populated in the filter table displayed below the browser section (along with their values). In this example, if you select sAMAccountName, the row in the filter table will show this attribute with a value of alice (assuming you picked Alice's record as a sample user node). Step 3 Enter value (optional) After Step 3, you have values for a specific record (Alice's record, in this case). Change the value to a dynamic session attribute that will help Policy Manager to associate a session with a specific record in LDAP/AD. For example, if you selected the sAMAccountName attribute in AD, click on the value field and select %{Authentication:Username}. When Policy Manager processes an authentication request % {Authentication:Username} is populated with the user ID of the user connecting to the network. Step 4 Add more attributes from the node of interest and continue with Step 2. AD/LDAP Configure Filter Attributes Tab The Attributes tab defines the attributes to be fetched from Active Directory or LDAP directory. Each attribute can also be "Enabled as Role," which means the value fetched for this attribute can be used directly in Enforcement Policies (See "Configuring Enforcement Policies " on page 229.) Dell Networking W-ClearPass Policy Manager 6.0 | User Guide 137