Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 96
X Wireless on Adding and Modifying Static Host Lists
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 96 highlights
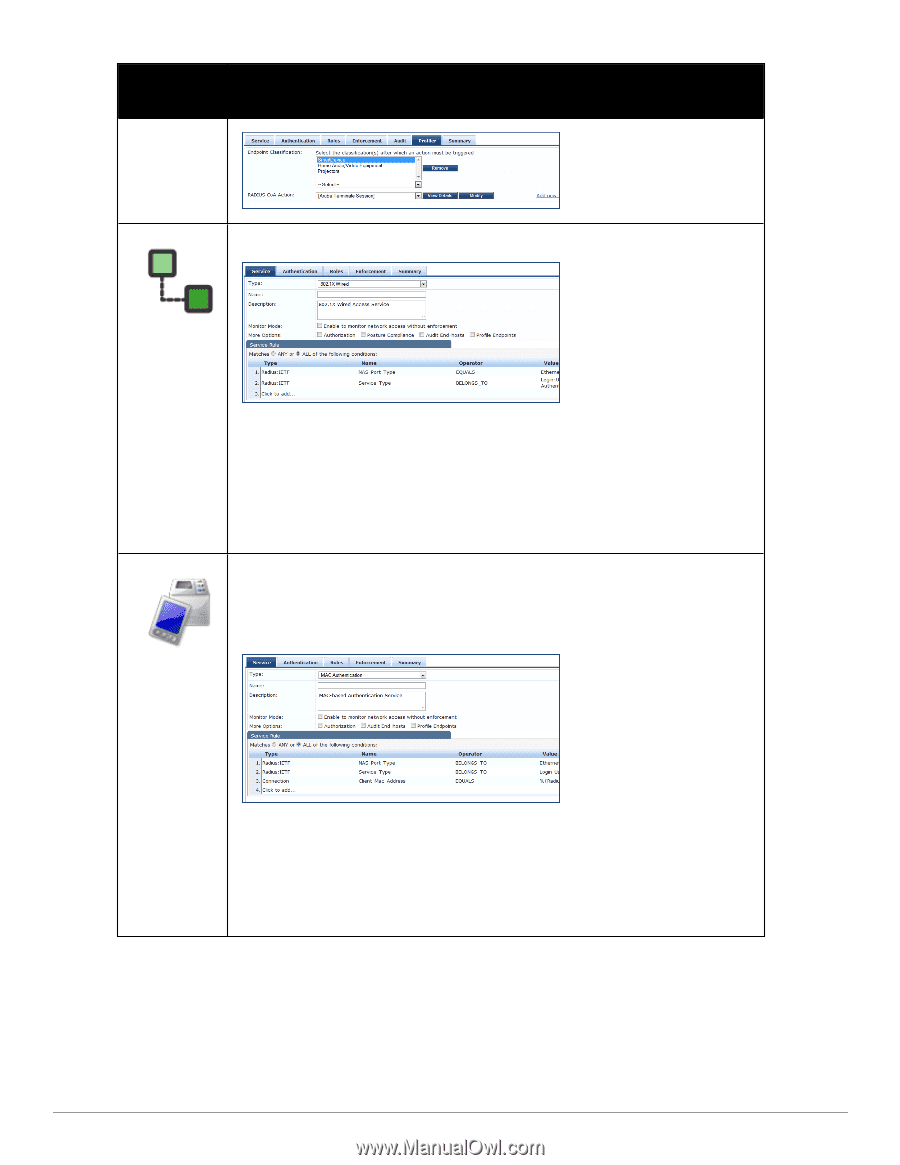
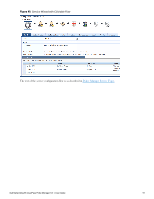
Service Type Description/ Available Policy Components (in tabs)/ Service Rule (in Rules Editor)/ Service-specific policy components (called out with legend below) For clients connecting through an Ethernet LAN, with authentication via IEEE 802.1X. 802.1X Wired MAC Authentication Except for the service rules shown above, configuration for the rest of the tabs is similar to the 802.1X Wireless Service. NOTE: If you want to administer the same set of policies for wired and wireless access, you can combine the service rule to define one single service. The other option is to keep two services for wired and wireless access, but re-use the policy components (authentication methods, authentication source, authorization source, role mapping policies, posture policies, and enforcement policies) in both services. Refer to the "802.1X Wireless " on page 92 service type for a description of the different tabs. MAC-based authentication service, for clients without an 802.1X supplicant or a posture agent (printers, other embedded devices, and computers owned by guests or contractors). The network access device sends a MAC authentication request to Policy Manager. Policy Manager can look up the client in a white list or a black list, authenticate and authorize the client against an external authentication/authorization source, and optionally perform an audit on the client. The default Authentication method used for this type of service is [MAC AUTH], which is a special type of method called MAC-AUTH. When this authentication method is selected, Policy Manager does stricter checking of the MAC Address of the client. This type of service can use either a built-in static host list (refer to "Adding and Modifying Static Host Lists " on page 166), or any other authentication source for the purpose of white-listing or black-listing the client. You can also specify the role mapping policy, based on categorization of the MAC addresses in the authorization sources. 96 Dell Networking W-ClearPass Policy Manager 6.0 | User Guide