Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 92
Policy Manager Service Types, Service Type
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 92 highlights
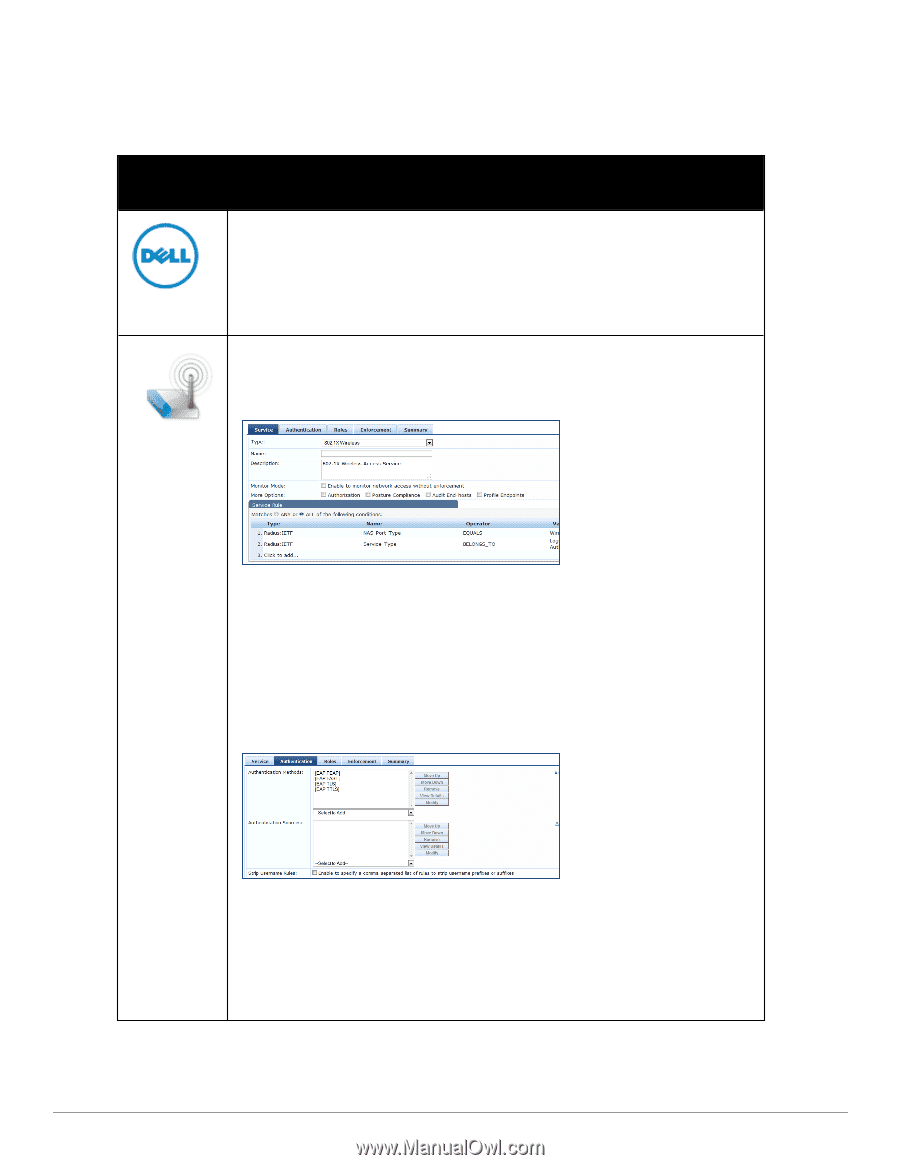
Policy Manager Service Types The following service types come preconfigured on Policy Manager: Table 39: Policy Manager Service Types Service Type Description/ Available Policy Components (in tabs)/ Service Rule (in Rules Editor)/ Service-specific policy components (called out with legend below) DellW-Series Wireless Template for wireless hosts connecting through a Dell W-Series 802.11 wireless access device or controller, with authentication via IEEE 802.1X. Service rules are customized for a typical Dell W-Series Mobility Controller deployment. Refer to the "802.1X Wireless " on page 92 service type for a description of the different tabs. For wireless clients connecting through an 802.11 wireless access device or controller, with authentication via IEEE 802.1X. By default, the template displays with the Service, Authentication, Roles, Enforcement, and Summary tabs. In the More Options section, click on Authorization, Posture Compliance, Audit End Hosts, or Profile Endpoints to enable additional tabs. 802.1X Wireless To configure authentication methods and authentication source, click on the Authentication tab. The Authentication methods used for this service depend on the 802.1X supplicants and the type of authentication methods you choose to deploy. The common types are PEAP, EAP-TLS, EAPFAST or EAP-TTLS (These methods are automatically selected). Non-tunneled EAP methods such as EAP-MD5 can also be used as authentication methods. The Authentication sources used for this type of service can be one or more instances of the following: Active Directory, LDAP Directory, SQL DB, Token Server or the Policy Manager local DB. For more information on configuring authentication sources, refer to "Adding and Modifying Authentication Sources " on page 127. You can enable Strip Username Rules to, optionally, pre-process the user name (to remove prefixes and suffixes) before authenticating and authorizing against the authentication source. To create an authorization source for this service click on the Authorization tab. This tab is not visible by default. To enable Authorization for this service select the Authorization check box on the Service tab. Policy Manager fetches role mapping attributes from the authorization sources associated with service, regardless of which authentication source was used to authenticate the user. For a given service, role mapping attributes are fetched from the following authorization sources: The authorization sources associated with the service. For more information on configuring authorization sources, refer to "Adding and Modifying Authentication Methods" on page 111. 92 Dell Networking W-ClearPass Policy Manager 6.0 | User Guide