Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 127
CHAP and EAP-MD5, Adding and Modifying Authentication Sources
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 127 highlights
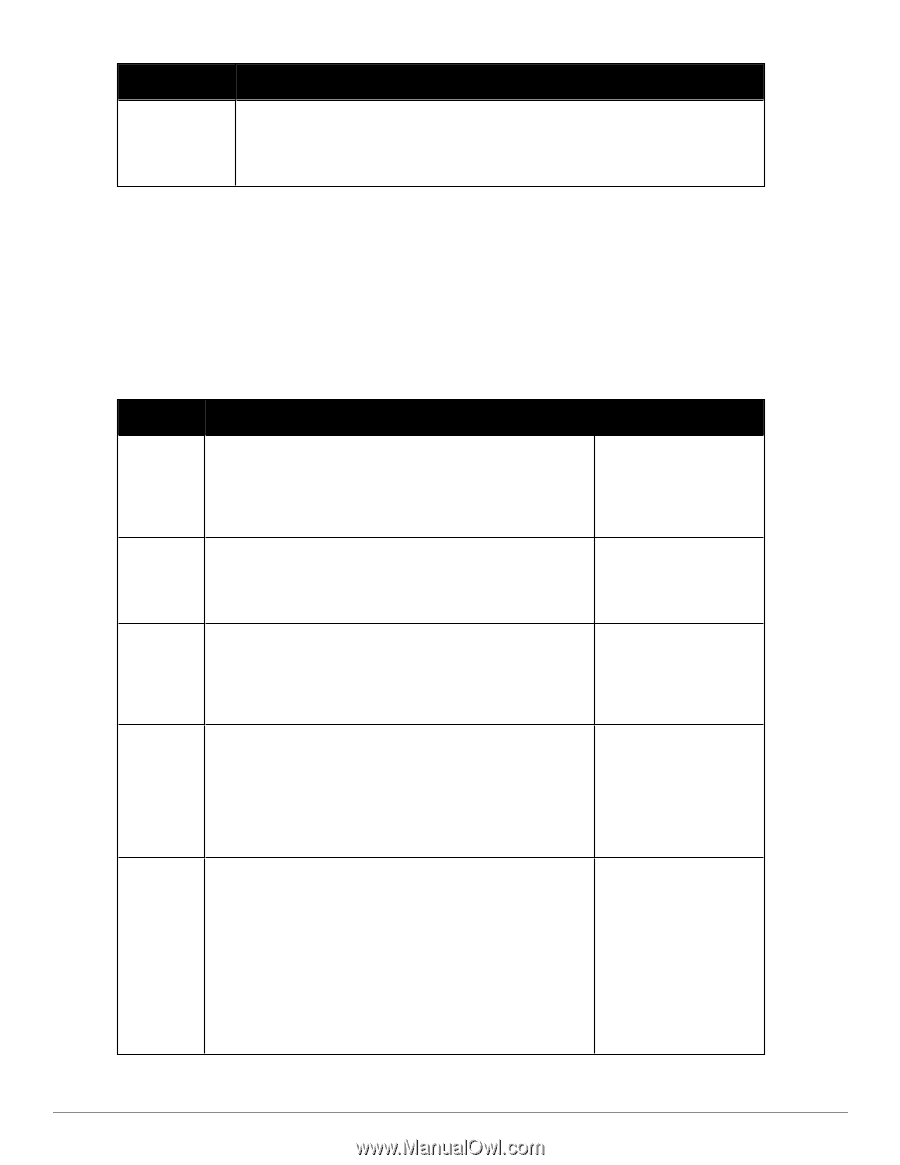
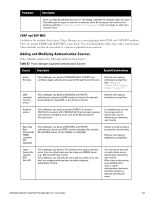
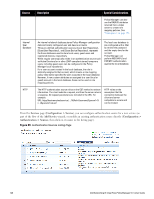
Parameter Description not in a configured authentication source. This setting is enabled, for example, when you want Policy Manager to trigger an audit for an unknown client. By turning on this check box and enabling audit (See "Configuring Audit Servers" on page 204), you can trigger an audit of an unknown client. CHAP and EAP-MD5 In addition the methods listed above, Policy Manager also comes packaged with CHAP and EAP-MD5 methods. These are named [CHAP] and [EAP-MD5], respectively. You can add methods of this type with a custom name. These methods can also be associated to a Service as authentication methods. Adding and Modifying Authentication Sources Policy Manager supports the following Authentication Sources: Table 57: Policy Manager Supported Authentication Sources Source Description Special Considerations Active Directory Policy Manager can perform NTLM/MSCHAPv2, PAP/GTC and certificate-based authentications against Microsoft Active Directory. Retrieve role mapping attributes by using filters. See "Adding and Modifying Role Mapping Policies " on page 155 LDAP compliant directory service Policy Manager can perform MSCHAPv2 and PAP/GTC authentication against any LDAP-compliant directory (for example, Novell eDirectory, OpenLDAP, or Sun Directory Server). Retrieve role mapping attributes by using filters.. Kerberos service Policy Manager can perform standard PAP/GTC or tunneled PAP/GTC (for example, EAP-PEAP[EAP-GTC]) authentication against any Kerberos 5 compliant server such as the Microsoft Active Directory server. It is mandatory to pair this Source type with an authorization source (identity store) containing user records. Open Data Base Connectivity (ODBC) compliant SQL databases Policy Manager can perform MSCHAPv2 and PAP/GTC authentication against any ODBC-compliant database (for example, Microsoft SQL Server, Oracle, MySQL, or PostgrSQL). Specify a stored procedure to query the relevant tables. Retrieve role mapping attributes by using filters. Token Servers (for example, RSA SecurID) Policy Manager can perform GTC authentication against any token server than can authenticate users by acting as a RADIUS server (e.g., RSA SecurID Token Server). Policy Manager can authenticate users against a token server and fetch role mapping attributes from any other configured Authorization Source. Pair this Source type with an authorization source (identity store) containing user records. When using a token server as an authentication source, use the administrative interface to optionally configure a separate authorization server. Dell Networking W-ClearPass Policy Manager 6.0 | User Guide 127