Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 104
Modifying Services,
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 104 highlights
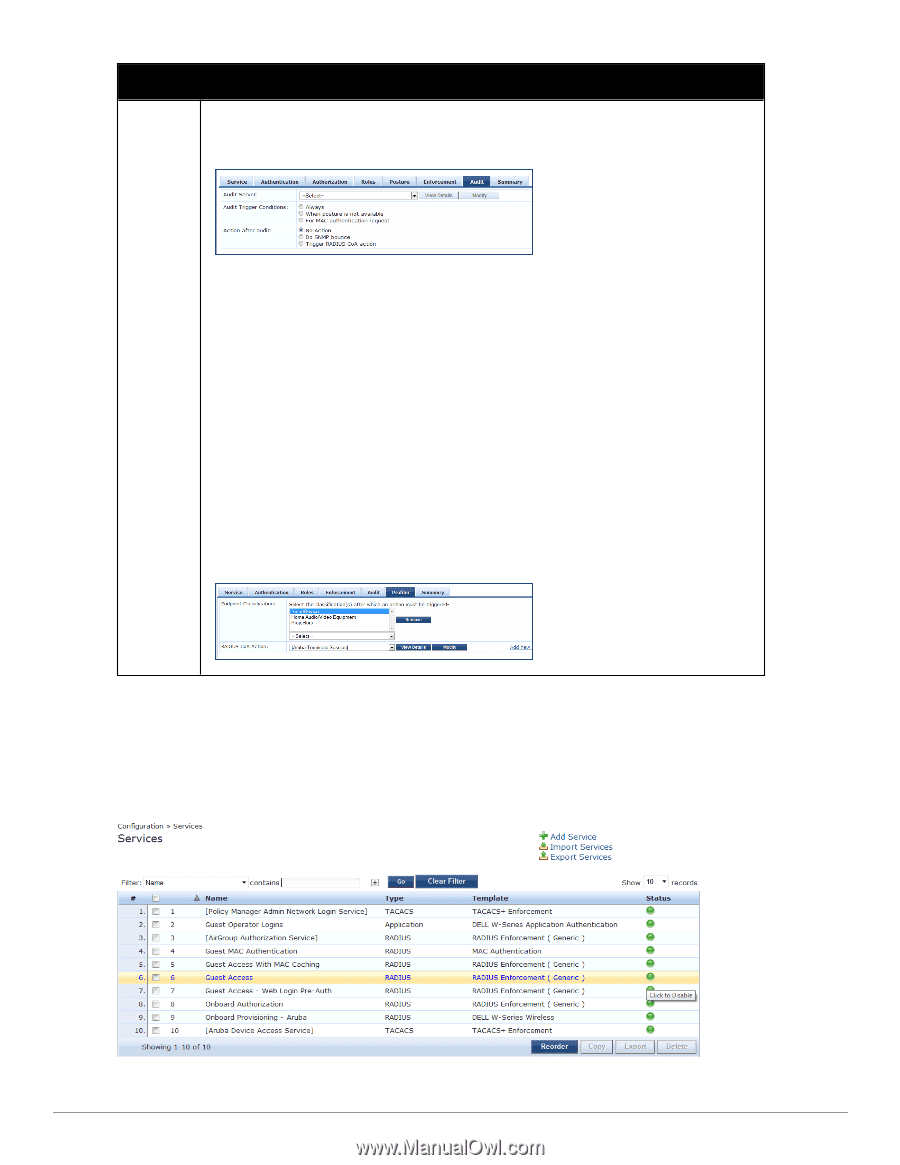
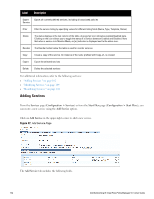
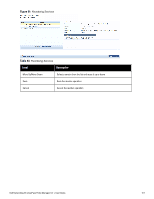
Label Description l Audit End-hosts: Select an Audit Server - either built-in or customized. Refer to "Configuring Audit Servers" on page 204 for audit server configuration steps. For this type of service you can perform audit Always, When posture is not available, or For MAC authentication requests. You can specify to trigger an audit always, when posture is not available, or for MAC authentication requests. If For MAC authentication requests is specified, then you can perform an audit For known end-hosts only or For unknown end hosts only, or For all end hosts. Known end hosts are defined as those clients that are found in the authentication source(s) associated with this service. Performing audit on a client is an asynchronous task, which means the audit can be performed only after the MAC authentication request has been completed and the client has acquired an IP address through DHCP. Once the audit results are available, there should be a way for Policy Manager to re-apply policies on the network device. This can be accomplished in one of the following ways: n No Action: The audit will not apply policies on the network device after this audit. n Do SNMP bounce: This option will bounce the switch port or to force an 802.1X reauthentication (both done via SNMP).Note: Bouncing the port triggers a new 802.1X/MAC authentication request by the client. If the audit server already has the posture token and attributes associated with this client in its cache, it returns the token and the attributes to Policy Manager. n Trigger RADIUS CoA action: This option sends a RADIUS Change of Authorization command to the network device by Policy Manager. l Optionally configure Profiler settings. Select one or more Endpoint Classification items from the drop down list, then select the RADIUS CoA action. You can also create a new action by selecting the Add new RADIUS CoA Action link. Modifying Services Navigate to the Configuration > Services page to view available services. You can use these service types as configured, or you can edit their settings. Figure 48: Service Listing Page 104 Dell Networking W-ClearPass Policy Manager 6.0 | User Guide