Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 99
Authorization, Posture Compliance, Audit End-hosts, Profile Endpoints, NOTE: Authentication, Posture
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 99 highlights
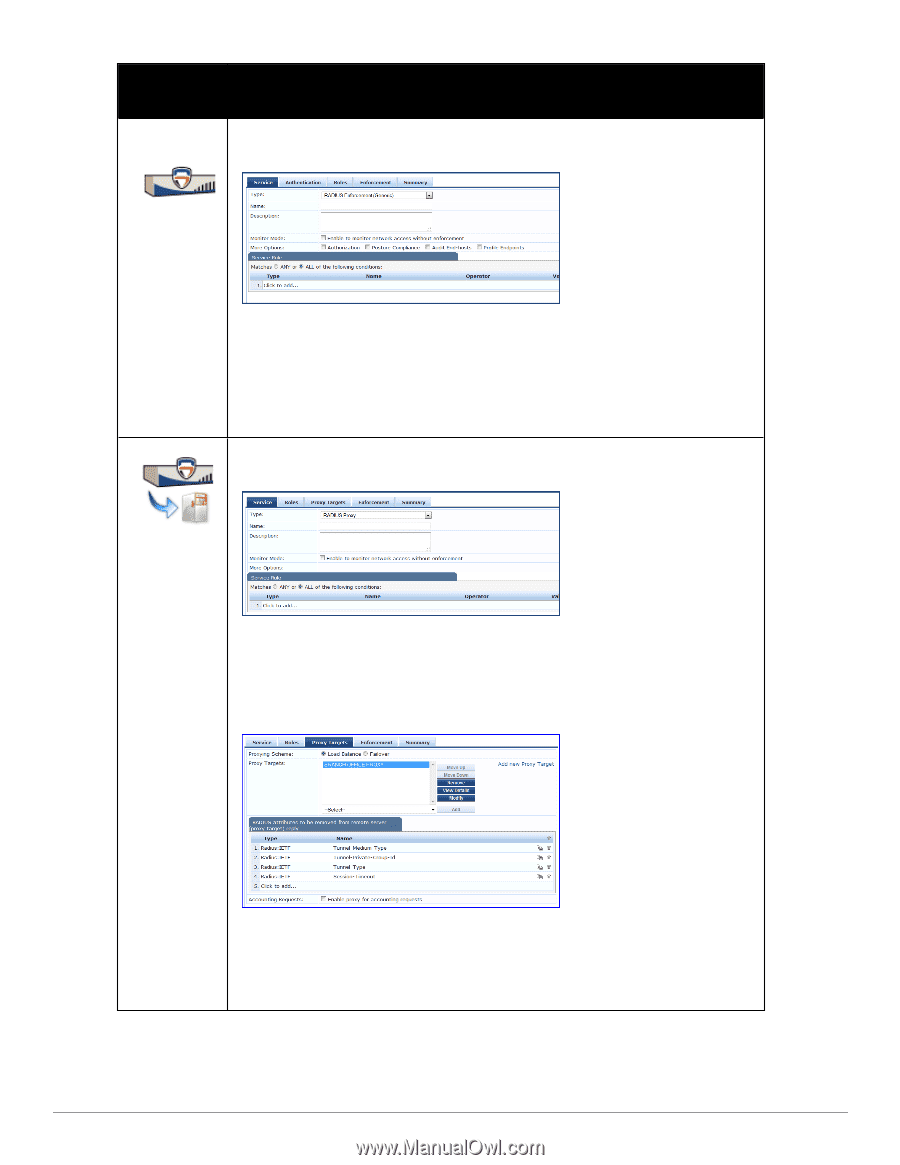
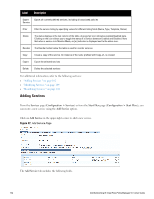
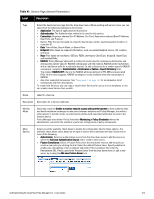
Service Type Description/ Available Policy Components (in tabs)/ Service Rule (in Rules Editor)/ Service-specific policy components (called out with legend below) Template for any kind of RADIUS request. Rules can be added to handle RADIUS requests that sends any type of standard or vendor-specific attributes. RADIUS Enforcement [Generic] NOTE: No default rule associated with this service type. Rules can be added to handle any type of standard or vendor-specific RADIUS attributes (any attribute that is loaded through the prepackaged vendor-specific or standard RADIUS dictionaries, or through other dictionaries imported into Policy Manager). You can click on the Authorization, Posture Compliance, Audit End-hosts and Profile Endpoints options to enable additional tabs. Refer to the "802.1X Wireless " on page 92 service type for a description of the other tabs. Template for any kind of RADIUS request that needs to be proxied to another RADIUS server (a Proxy Target). RADIUS Proxy NOTE: No default rule is associated with this service type. Rules can be added to handle any type of standard or vendor-specific RADIUS attributes. Typically, proxying is based on a realm or domain of the user trying to access the network. NOTE: Authentication, Posture, and Audit tabs are not available for this service type. Role mapping rules can be created based on the RADIUS attributes that are returned by the proxy target (using standard or vendor-specific RADIUS attributes). The servers to which requests are proxied are called Proxy Targets. Requests can be dispatched to the proxy targets randomly; over time these requests are Load Balanced. Instead, in the Failover mode, requests can be dispatched to the first proxy target in the ordered list of targets, and then subsequently to the other proxy targets, sequentially, if the prior requests failed. When you Enable proxy for accounting requests accounting requests are also sent to the proxy targets. Dell Networking W-ClearPass Policy Manager 6.0 | User Guide 99