Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 206
Modifying Built-In Audit Servers,
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 206 highlights
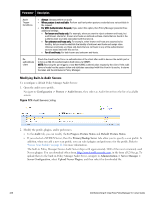
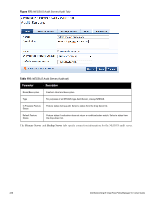
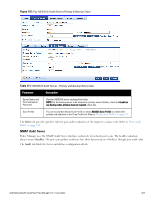
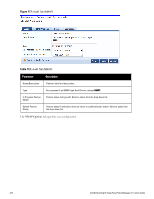
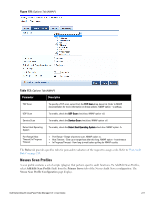
Parameter Description Audit Trigger Conditions l Always: Always perform an audit l When posture is not available: Perform audit only when posture credentials are not available in the request. l For MAC Authentication Request, If you select this option, then Policy Manager presents three additional settings: n For known end-hosts only. For example, when you want to reject unknown end-hosts, but audit known clients for. Known end-hosts are defined as those clients that are found in the authentication source(s) associated with this service. n For unknown end-hosts only. For example, when known end-hosts are assumed to be healthy, but you want to establish the identity of unknown end-hosts and assign roles. Unknown end-hosts are those end-hosts that are not found in any of the authentication sources associated with this service. n For all end-hosts. For both known and unknown end-hosts. Reauthenticate client Check the check box for Force re-authentication of the client after audit to bounce the switch port or to force an 802.1X reauthentication (both done via SNMP). NOTE: Bouncing the port triggers a new 802.1X/MAC authentication request by the client. If the audit server already has the posture token and attributes associated with this client in its cache, it returns the token and the attributes to Policy Manager. Modifying Built-In Audit Servers To reconfigure a default Policy Manager Audit Servers: 1. Open the audit server profile. Navigate to Configuration > Posture > Audit Servers, then select an Audit Server from the list of available servers. Figure 173: Audit Servers Listing 2. Modify the profile, plugins, and/or preferences. l In the Audit tab, you can modify the In Progress Posture Status and Default Posture Status. l If you selected a NESSUS Server, then the Primary/Backup Server tabs allow you to specify a scan profile. In addition, when you add a new scan profile, you can select plugins and preferences for the profile. Refer to "Nessus Scan Profiles" on page 211 for more information. The built-in Policy Manager Nessus Audit Server ships with approximately 1000 of the most commonly used Nessus plugins. You can download others from http://www.tenablesecurity.com, in the form all-2.0.tar.gz. To upload them to the built-in Policy Manager Audit Server, navigate to Administration > Server Manager > Server Configuration, select Upload Nessus Plugins, and then select the downloaded file. 206 Dell Networking W-ClearPass Policy Manager 6.0 | User Guide