Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 55
Table 19, Service Categorization, Role Mapping, Posture Validation, Audit
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 55 highlights
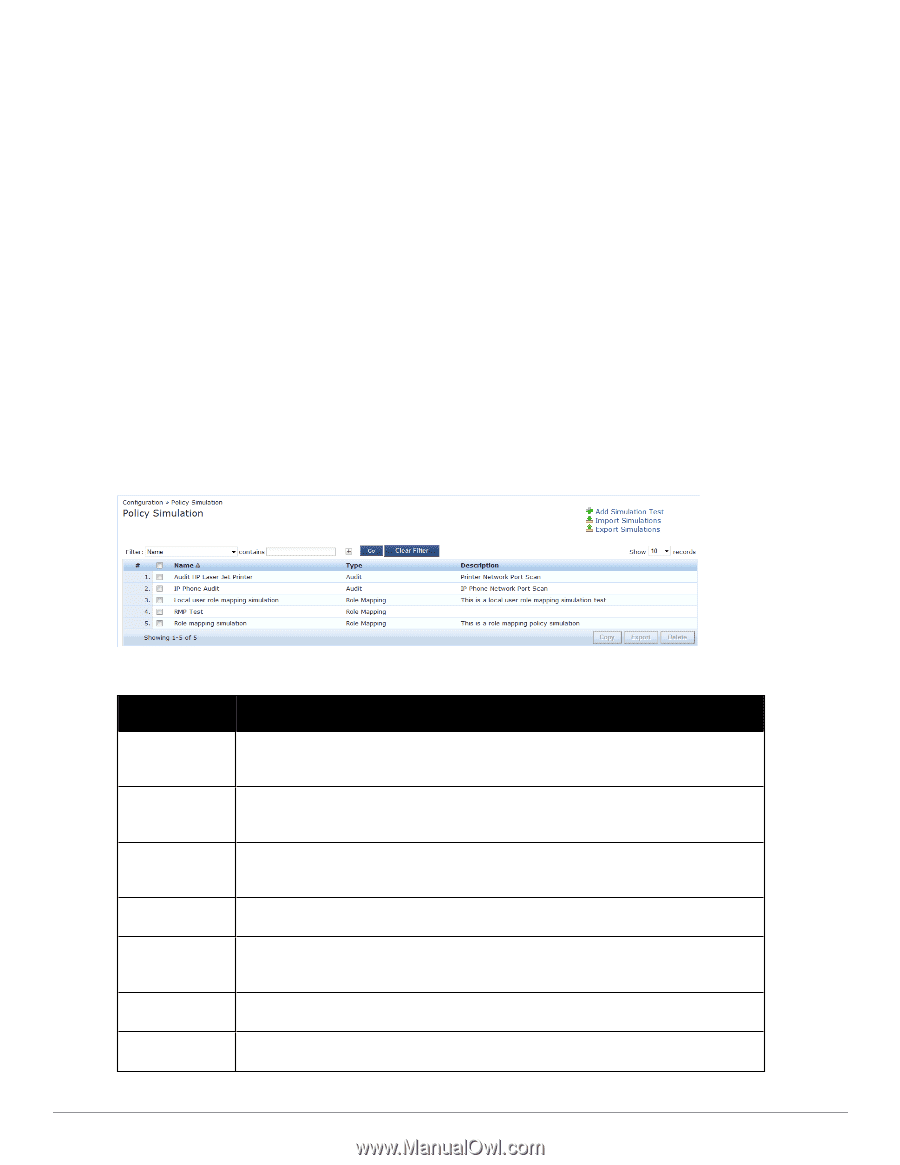
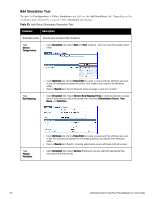
l Service Categorization - A service categorization simulation allows you to specify a set of attributes in the RADIUS or Connection namespace and test which configured service the request will be categorized into. The request attributes that you specify represent the attributes sent in the simulated request. l Role Mapping - Given the service name (and associated role mapping policy), the authentication source and the user name, the role mapping simulation maps the user into a role or set of roles. You can also use the role mapping simulation to test whether the specified authentication source is reachable. l Posture Validation - A posture validation simulation allows you to specify a set of posture attributes in the posture namespace and test the posture status of the request. The posture attributes that you specify represent the attributes sent in the simulated request. l Audit - An audit simulation allows you to specify an audit server (Nessus- or NMAP-based) and the IP address of the device you want to audit. An audit simulation triggers an audit on the specified device and displays the results. l Enforcement Policy - Given the service name (and the associated enforcement policy), a role or a set of roles, the system posture status, and an optional date and time, the enforcement policy simulation evaluates the rules in the enforcement policy and displays the resulting enforcement profiles and their contents. l Chained Simulation - Given the service name, authentication source, user name, and an optional date and time, the chained simulation combines the results of role mapping, posture validation and enforcement policy simulations and displays the corresponding results. Figure 32: Policy Simulation Table 19: Policy Simulation Container Description Add Simulation Test Opens the Add Simulation Test page. Import Simulations Opens the Import Simulations popup. Export Simulations Opens the Export Simulations popup. Filter Select the filter by which to constrain the display of simulation data. Copy Make a copy the selected policy simulation. The copied simulation is renamed with a prefix of Copy_Of_. Export Opens the Export popup. Delete Click to delete a selected (check box on left) Policy Simulation. Dell Networking W-ClearPass Policy Manager 6.0 | User Guide 55