Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 65
Profiling, Stage 1, Example, Post Profile Actions, Fingerprint Dictionaries,
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 65 highlights
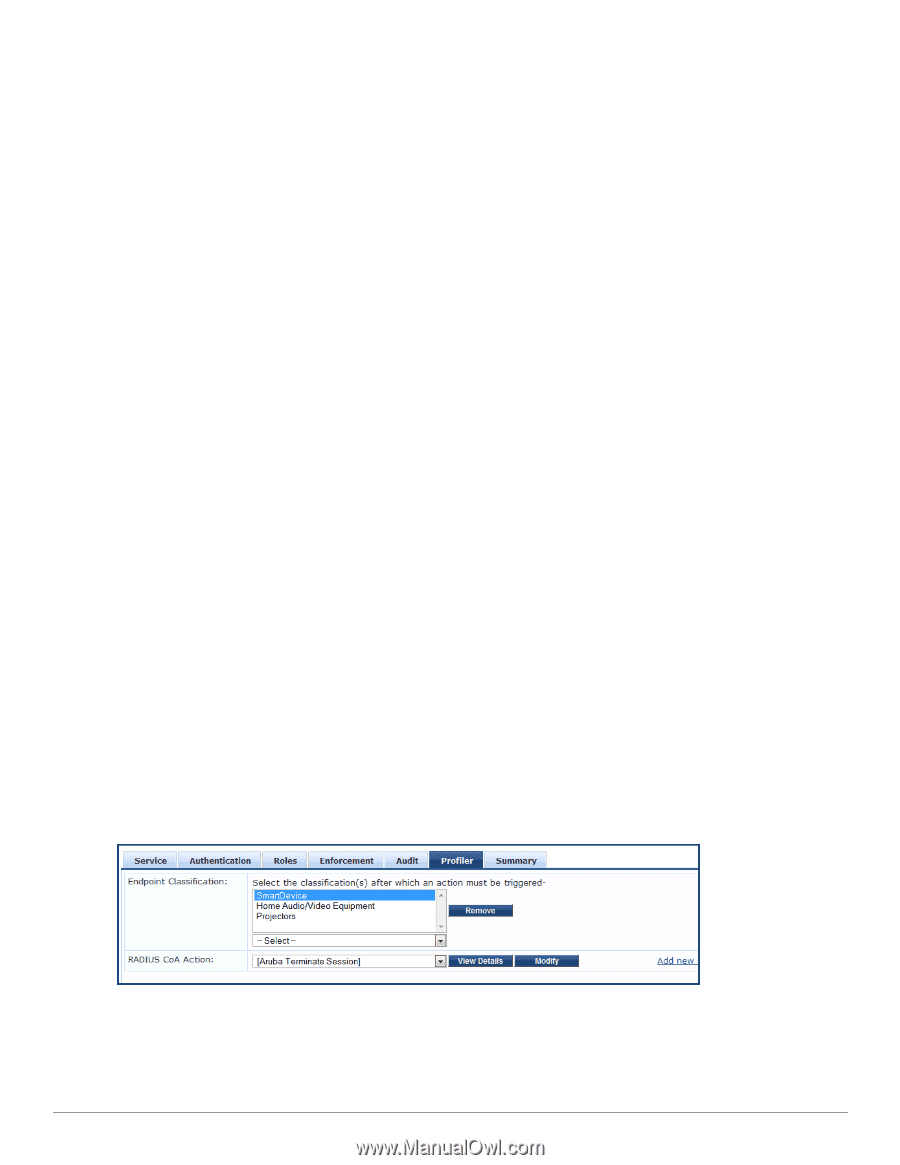
Profiling The Profile module uses a two-stage approach to classify endpoints using input attributes. Stage 1 Stage 1 tries to derive device-profiles using static dictionary lookups. Based on the attributes available, it will lookup dhcp, http, active_sync, MAC oui, and SNMP dictionaries and derives multiple matching profiles. When multiple matches are returned, the priority of the source that provided the attribute is used to select the appropriate profile. The following list shows the decreasing order of priority. l OnGuard/ActiveSync plugin l HTTP User-Agent l SNMP l DHCP l MAC OUI Stage 2 CPPM comes with a built-in set of rules which evaluates to a device-profile. Rules engine uses all input attributes and device profiles from Stage 1. The resulting rule evaluation may or may not result in a profile. Stage-2 is intended to refine the results of profiling. Example With DHCP options Stage-1 can identify that a device is Android. Stage-2 uses rules to combine this with MAC OUI to further classify an android device as Samsung Android, HTC Android etc. Post Profile Actions After profiling an endpoint, profiler can be configured to perform CoA on the Network Device to which an endpoint is connected. Post profile configurations are configured under Service. The administrator can select a set of categories and a CoA profile to be applied when the profile matches one of the selected categories. CoA is triggered using the selected CoA profile. Any option from Endpoint Classification can be used to invoke CoA on a change of any one of the fields (category, family, and name). Figure 38: Services > Edit > Profiler tab settings Fingerprint Dictionaries CPPM uses a set of dictionaries and built-in rules to perform device fingerprinting. The following dictionaries are Dell Networking W-ClearPass Policy Manager 6.0 | User Guide 65