Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Manager 6 - Page 217
Enforcement, Enforcement Architecture and Flow
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 217 highlights
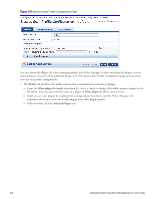
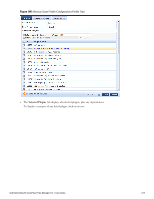
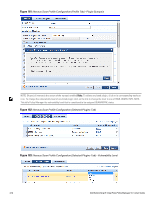
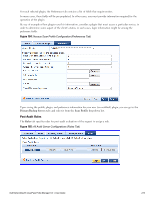
Chapter 17 Enforcement Policy Manager controls network access by sending a set of access-control attributes to the request-originating Network Access Device (NAD). Policy Manager sends these attributes by evaluating an Enfocement Policy associated with the service. The evaluation of Enforcement Policy results in one or more Enforcement Profiles; each Enforcement Profile wraps the access control attributes sent to the Network Access Device. For example, for RADIUS requests, commonly used Enforcement Profiles include attributes for VLAN, Filter ID, Downloadable ACL and Proxy ACL. Enforcement Architecture and Flow To evaluate a request, a Policy Manager Application assembles the request's client roles, client posture (system posture token), and system time. The calculation that matches these components to a pre-defined Enforcement Profile occurs inside of a black box called an Enforcement Policy. Each Enforcement Policy contains a rule or set of rules for matching Conditions (role, posture and time) to Actions (Enforcement Profiles). For each request, it yields one or more matches, in the form of Enforcement Profiles, from which Policy Manager assembles access-control attributes for return to the originating NAD, subject to the following disambiguation rules: l If an attribute occurs only once within an Enforcement Profile, transmit as is. l If an attribute occurs multiple times within the same Enforcement Profile, transmit as a multi-valued attribute. l If an attribute occurs in more than one Enforcement Profile, only transmit the value from the first Enforcement Profile in priority order. NOTE: Optionally, each Enforcement Profile can have an associated group of NADs; when this occurs, Enforcement Profiles are only sent if the request is received from one of the NADs in the group. For example, you can have the same rule for VPN, LAN and WLAN access, with enforcement profiles associated with device groups for each type of access. If a device group is not associated with the enforcement profile, attributes in that profile are sent regardless of where the request originated. Dell Networking W-ClearPass Policy Manager 6.0 | User Guide 217