HP Xw460c HP Integrated Lights-Out 2 User Guide for Firmware 1.75 and 1.77 - Page 170
How user time restrictions are enforced, Creating multiple restrictions and roles
 |
View all HP Xw460c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 170 highlights
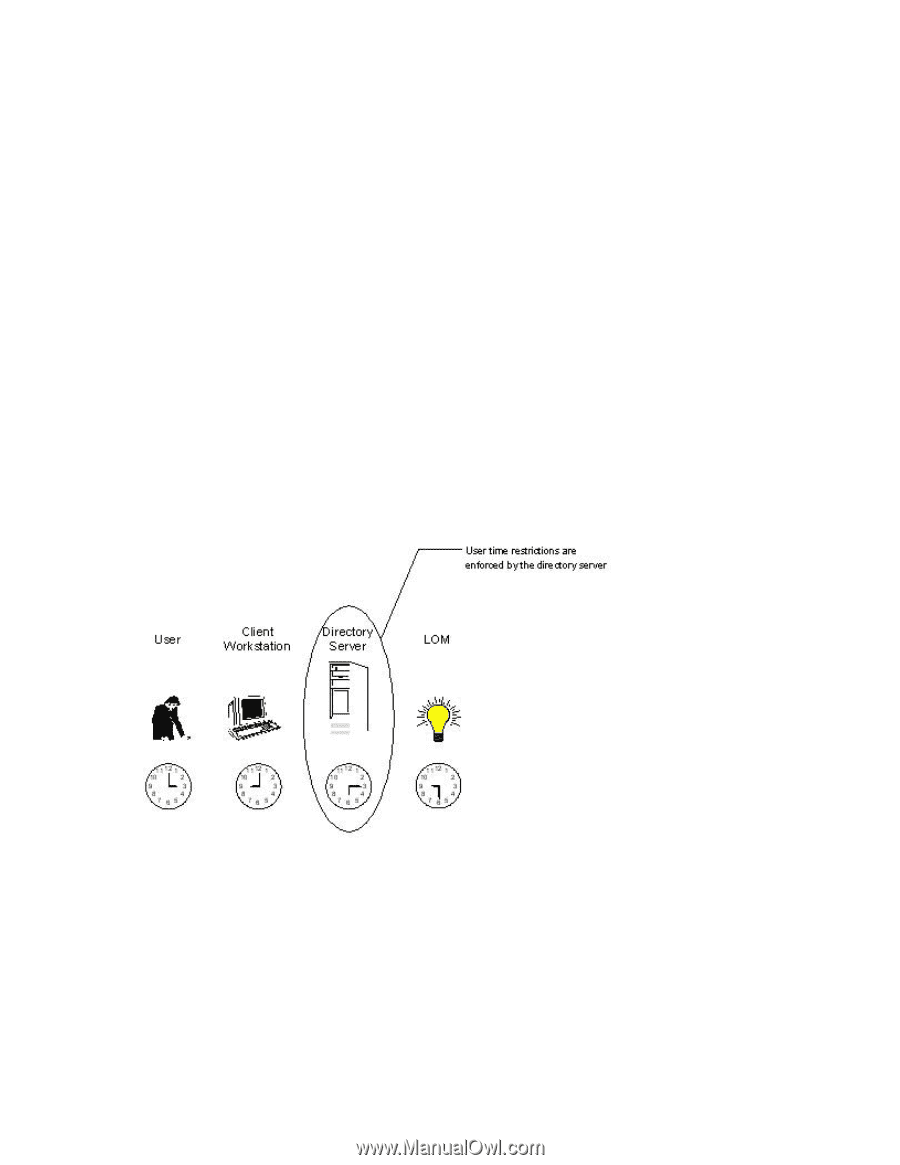
name server. If the name service goes down or cannot be reached, DNS restrictions cannot be matched and will fail. DNS-based restrictions can limit access to a single, specific machine name or to machines sharing a common domain suffix. For example, the DNS restriction, www.hp.com, matches hosts that are assigned the domain name www.hp.com. However, the DNS restriction, *.hp.com, matches any machine originating from HP. DNS restrictions can cause some ambiguity because a host can be multi-homed. DNS restrictions do not necessarily match one-to-one with a single system. Using DNS-based restrictions can create some security complications. Name service protocols are insecure. Any individual with malicious intent and access to the network can place a rogue DNS service on the network creating fake address restriction criteria. Organizational security policies should be taken into consideration when implementing DNS-based address restrictions. How user time restrictions are enforced Administrators can place a time restriction on directory user accounts. Time restrictions limit the ability of the user to log in (authenticate) to the directory. Typically, time restrictions are enforced using the time at the directory server, but if the directory server is located in a different time zone or a replica in a different time zone is accessed, then time zone information from the managed object can be used to adjust for relative time. The directory server evaluates user time restrictions, but the determination can be complicated by time zone changes or authentication mechanism. Creating multiple restrictions and roles The most useful application of multiple roles includes restricting one or more roles so that rights do not apply in all situations. Other roles provide different rights under different constraints. Using multiple restrictions and roles enables the administrator to create arbitrary, complex rights relationships with a minimum number of roles. For example, an organization might have a security policy in which LOM administrators are allowed to use the LOM device from within the corporate network but are only able to reset the server outside of regular business hours. Directory-enabled remote management 170