Netgear GS716Tv2 GS716Tv2/GS724Tv3 Software Admin Manual - Page 149
X Configuration, Authenticators, Supplicants, Authentication Server, Security
 |
View all Netgear GS716Tv2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 149 highlights
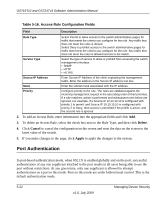
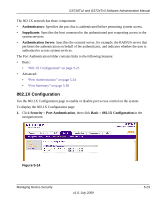
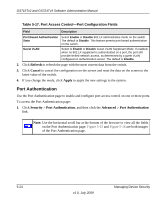
GS716Tv2 and GS724Tv3 Software Administration Manual The 802.1X network has three components: • Authenticators: Specifies the port that is authenticated before permitting system access. • Supplicants: Specifies the host connected to the authenticated port requesting access to the system services. • Authentication Server: Specifies the external server, for example, the RADIUS server that performs the authentication on behalf of the authenticator, and indicates whether the user is authorized to access system services. The Port Authentication folder contains links to the following features: • Basic: • "802.1X Configuration" on page 5-23 • Advanced: • "Port Authentication" on page 5-24 • "Port Summary" on page 5-28 802.1X Configuration Use the 802.1X Configuration page to enable or disable port access control on the system. To display the 802.1X Configuration page: 1. Click Security Port Authentication, then click Basic 802.1X Configuration in the navigation tree. Figure 5-14 Managing Device Security v1.0, July 2009 5-23