Netgear GS716Tv2 GS716Tv2/GS724Tv3 Software Admin Manual - Page 235
Authenticator, Supplicant, Authentication server, Additionally, there exists a third role
 |
View all Netgear GS716Tv2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 235 highlights
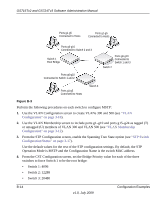
GS716Tv2 and GS724Tv3 Software Administration Manual The ports of an 802.1X authenticator switch provide the means in which it can offer services to other systems reachable via the LAN. Port-based network access control allows the operation of a switch's ports to be controlled in order to ensure that access to its services is only permitted by systems that are authorized to do so. Port access control provides a means of preventing unauthorized access by supplicants to the services offered by a system. Control over the access to a switch and the LAN to which it is connected can be desirable in order to restrict access to publicly accessible bridge ports or to restrict access to departmental LANs. Access control is achieved by enforcing authentication of supplicants that are attached to an authenticator's controlled ports. The result of the authentication process determines whether the supplicant is authorized to access services on that controlled port. A Port Access Entity (PAE) is able to adopt one of two distinct roles within an access control interaction: 1. Authenticator: A Port that enforces authentication before allowing access to services available via that Port. 2. Supplicant: A Port that attempts to access services offered by the Authenticator. Additionally, there exists a third role: 3. Authentication server: Performs the authentication function necessary to check the credentials of the Supplicant on behalf of the Authenticator. All three roles are required in order to complete an authentication exchange. GS716T/GS724T switches support the Authenticator role only, in which the PAE is responsible for communicating with the Supplicant. The Authenticator PAE is also responsible for submitting the information received from the Supplicant to the Authentication Server in order for the credentials to be checked, which will determine the authorization state of the Port. The Authenticator PAE controls the authorized/unauthorized state of the controlled Port depending on the outcome of the authentication process, such as Local and/or RADIUS. Configuration Examples B-9 v1.0, July 2009