McAfee EPOCDE-AA-BA Product Guide - Page 286
Renaming subnets, Viewing detected subnets and their details
 |
View all McAfee EPOCDE-AA-BA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 286 highlights
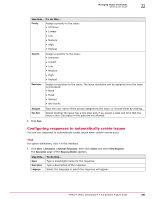
21 Detecting Rogue Systems Rogue System Detection command-line options Task 1 Click Menu | Reporting | Queries & Reports, and query for any ignored subnets. For more information on working with queries, see Reporting on System Status. 2 On the Unsaved Queries page, click Include. 3 In the Include dialog box, click OK. Renaming subnets Use this task to rename subnets. This task can be performed from: Detected Subnets Details page Detected Subnets page Getting there Click Menu | Systems | Detected Systems, click any subnet category in the Subnet Status monitor, then click any subnet. Click Menu | Systems | Detected Systems, then click any subnet category in the Subnet Status monitor. For option definitions, click ? in the interface. Task 1 Select the subnet you want to rename, then click Actions and select Detected Systems | Rename. 2 In the Rename dialog box, type the new name for the subnet, then click OK. Viewing detected subnets and their details Use this task to view detected subnets and their details. You can view detected subnets details from any page that displays detected subnets. For option definitions, click ? in the interface. Task 1 Click Menu | Systems | Detected Systems. 2 In the Subnet Status monitor, click any category to view the list of detected subnets it contains, such as Covered. The Detected Subnets page appears and displays the subnets in that category. 3 Click any detected subnet to view its details. The Detected Subnet Details page appears. Rogue System Detection command-line options You can run command-line options from the client system. You can start the sensor manually from the command-line instead of starting it as a Windows service. You might want to do this if you are testing functionality, or to check the sensor version. The following table lists the run-time command-line options for the sensor. Switch --console --help --install Description Forces the sensor to run as a normal command-line executable; otherwise it must be run as an NT service. Prints the Help screen and lists available command-line options. Registers the sensor with the Windows Service Control Manager. 286 McAfee® ePolicy Orchestrator® 4.6.0 Software Product Guide