Netgear GS724Tv4 Software Administration Manual - Page 217
Src IP Mask, Src IP Address
 |
View all Netgear GS724Tv4 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 217 highlights
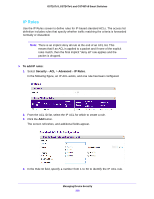
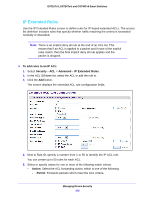
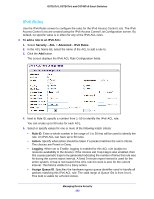
GS716Tv3, GS724Tv4, and GS748Tv5 Smart Switches 5. Select or specify values for one or more of the following match criteria: • Rule ID. Specify a number from 1-50 to identify the IP ACL rule. You can create up to 50 rules for each ACL. • Action. Select the ACL forwarding action, which is one of the following: - Permit. Forward packets which meet the ACL criteria. - Deny. Drop packets which meet the ACL criteria. • Egress Queue. The hardware egress queue identifier used to handle all packets matching this ACL rule. • Logging. When set to Enable, logging is enabled for this ACL rule (subject to resource availability in the device). If the Access List Trap Flag is also enabled, then this causes periodic traps to be generated indicating the number of times this rule was hit during the current report interval. A fixed 5-minute report interval is used for the entire system. A trap is not issued if the ACL rule hit count is zero for the current interval. This field is visible for a Deny action. • Match Every. Require a packet to match the criteria of this ACL. Select True or False from the drop-down list. Match Every is exclusive to the other filtering rules, so if Match Every is True, the other rules on the screen are not available. • Src IP Address. Require a packet's source IP address to match the address listed here. Enter an IP Address in the appropriate field using dotted-decimal notation. The address you enter is compared to a packet's source IP Address. • Src IP Mask. Specify the source IP address wildcard mask. Wild card masks determine which bits are used and which bits are ignored. A wild card mask of 255.255.255.255 indicates that no bit is important. A wildcard of 0.0.0.0 indicates that all of the bits are important. Wildcard masking for ACLs operates differently from a subnet mask. A wildcard mask is in essence the inverse of a subnet mask. For example, to apply the rule to all hosts in the 192.168.1.0/24 subnet, enter 0.0.0.255 in the Source IP Mask field. This field is required when you configure a source IP address. 6. Click the Apply button. To modify the match criteria for an ACL rule: 1. From the ACL Name list on the IP Rules screen, select the ACL that includes the rule to update. 2. In the Basic ACL Rule Table, click the rule ID. The rule ID is a hyperlink to the Standard ACL Rule Configuration screen. 3. Modify the ACL rule information. 4. Click the Apply button. To delete and IP ACL rule: 1. In the Basic ACL Rule Table on the IP Rules screen, select the check box associated with the rule to remove. 2. Click the Delete button. Managing Device Security 217