Netgear GS724Tv4 Software Administration Manual - Page 219
Source L4 Port Number, Destination L4 Port Number
 |
View all Netgear GS724Tv4 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 219 highlights
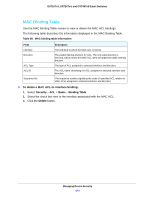
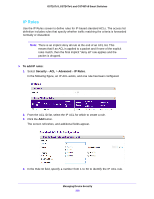
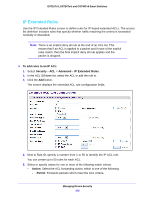
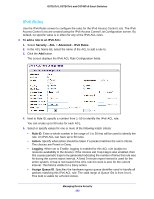
GS716Tv3, GS724Tv4, and GS748Tv5 Smart Switches - Deny. Drops packets which meet the ACL criteria. • Egress Queue. Specify the hardware egress queue identifier used to handle all packets matching this ACL rule. • Match Every. Require a packet to match the criteria of this ACL. Select True or False from the drop-down menu. Match Every is exclusive to the other filtering rules, so if Match Every is True, the other rules on the screen are not available. • Protocol Type. Require a packet's protocol to match the protocol listed here. Select a type from the drop-down menu or enter the protocol number in the available field. • Src IP Address. Require a packet's source IP address to match the address listed here. Type an IP Address in the appropriate field using dotted-decimal notation. The address you enter is compared to a packet's source IP Address. • Src IP Mask. Specify the source IP address wildcard mask. Wild card masks determines which bits are used and which bits are ignored. A wild card mask of 255.255.255.255 indicates that no bit is important. A wildcard of 0.0.0.0 indicates that all of the bits are important. Wildcard masking for ACLs operates differently from a subnet mask. A wildcard mask is in essence the inverse of a subnet mask. For example, to apply the rule to all hosts in the 192.168.1.0/24 subnet, you type 0.0.0.255 in the Source IP Mask field. This field is required when you configure a source IP address. • Src L4 Port. Require a packet's TCP/UDP source port to match the port listed here. Click Complete one of the following fields: - Source L4 Keyword. Select the desired L4 keyword from a list of source ports on which the rule can be based. - Source L4 Port Number. If the source L4 keyword is Other, enter a user-defined Port ID by which packets are matched to the rule. • Dst IP Address. Require a packet's destination port IP address to match the address listed here. Enter an IP Address in the appropriate field using dotted-decimal notation. The address you enter is compared to a packet's destination IP Address. • Dst IP Mask. Specify the destination IP address wildcard mask. Wild card masks determines which bits are used and which bits are ignored. A wild card mask of 255.255.255.255 indicates that no bit is important. A wildcard of 0.0.0.0 indicates that all of the bits are important. Wildcard masking for ACLs operates differently from a subnet mask. A wildcard mask is in essence the inverse of a subnet mask. For example, to apply the rule to all hosts in the 192.168.1.0/24 subnet, you type 0.0.0.255 in the Source IP Mask field. This field is required when you configure a source IP address. • Dst L4 Port. Require a packet's TCP/UDP destination port to match the port listed here. Complete one of the following fields: - Destination L4 Keyword. Select the desired L4 keyword from a list of destination ports on which the rule can be based. - Destination L4 Port Number. If the destination L4 keyword is Other, enter a user-defined Port ID by which packets are matched to the rule. • Service Type. Select one of the Service Type match conditions for the extended IP ACL rule. The possible values are IP DSCP, IP precedence, and IP TOS, which are Managing Device Security 219