Dell PowerEdge 2321DS User Manual - Page 204
LDAP SSL Certificates, Enabling SSL on a Domain Controller
 |
View all Dell PowerEdge 2321DS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 204 highlights
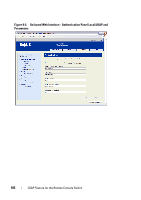
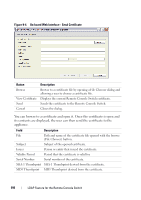
Access Control Attribute (Standard schema set only) The value of this field specifies which attribute in the LDAP directory is to be used to contain discretionary access control information and is only enabled when Standard Schema is selected. The Access Control Attribute is chosen from among the attributes in the LDAP directory object representing the group whose membership includes both the user and the appliance or attached computer that you are trying to access. When using the Standard schema, it is necessary for Group objects in the Group Container to have an attribute that is chosen to contain the permission level associated with the Group. The Access Control Attribute field, available when the Standard schema is selected, contains the name of the chosen attribute. The chosen attribute must be capable of storing a character string value; for example, the default attribute is "info" which is an attribute accessible via the Active Directory Users and Computers (ADUC) snap-in. Using ADUC, the value of the info attribute is set by accessing the "Notes" property of the Group object. LDAP SSL Certificates All LDAP protocol exchanges (between a Remote Console Switch and Active Directory servers) are secured by SSL. When the LDAP protocol is being protected by SSL, it is referred to as LDAPS (Lightweight Directory Access Protocol over SSL). Each LDAPS connection begins with a protocol handshake that triggers a security certificate transmission from the responding Active Directory server to the Remote Console Switch. Once received, the Remote Console Switch is responsible for verifying the certificate. In order to verify the certificate, the appliance must be configured with a copy of the root Certification Authority's (CA) certificate. Before this can be done, the certificate must first be generated. Enabling SSL on a Domain Controller If you plan to use Microsoft Enterprise Root CA to automatically assign all your domain controllers SSL certificate, you must perform the following steps to enable SSL on each domain controller if you have not previously done so. 1 Install a Microsoft Enterprise Root CA on a Domain Controller. 187 LDAP Feature for the Remote Console Switch