Dell PowerEdge 2321DS User Manual - Page 213
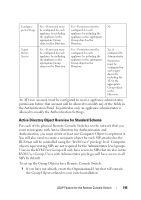
Active Directory Object Overview for Standard Schema
 |
View all Dell PowerEdge 2321DS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 213 highlights
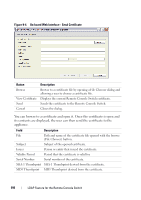
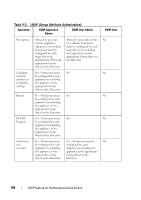
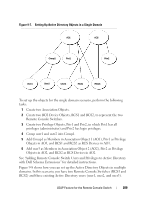
Configure Yes - Permission must Yes - Permission must be No port settings be configured for each configured for each appliance by including appliance by including the the appliance in the appliance in the appropriate appropriate Group Group object in the object in the Directory. Directory. Target Device Access Yes - Permission must be configured for each appliance by including the appliance in the appropriate Group object in the Directory. Yes - Permission must be configured for each appliance by including the appliance in the appropriate Group object in the Directory. Yes, if configured by Administrator Permission must be configured for each target device by including the TD in the appropriate Group object in the Directory. An AD user account must be configured to receive appliance administrator permission before that account will be allowed to modify any of the fields in the Authentication Panel. In particular, only an appliance administrator is allowed to modify the Authentication Settings. Active Directory Object Overview for Standard Schema For each of the physical Remote Console Switches on the network that you want to integrate with Active Directory for Authentication and Authorization, you must create at least one Computer Object to represent it. You will also need to create a computer object for each SIP attached to the RCS that will be controlled using the "KVM User" privilege level. Computer objects representing SIPs are not required for the Administrator level groups. Users in the KVM User Group will only have access to SIPs that are also in the KVM User Group. Users with Administrator privileges will have access to all SIPs by default. To set up the Group Objects for a Remote Console Switch: 1 If you have not already, create the Organizational Unit that will contain the Group Objects related to your switch installation. LDAP Feature for the Remote Console Switch 196