D-Link DGS-3426P Product Manual - Page 289
IP-MAC-Port Binding, General Overview, Common IP Management Security Issues
 |
UPC - 790069291982
View all D-Link DGS-3426P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 289 highlights
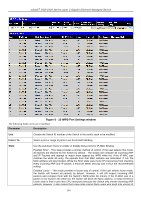
xStack® DGS-3400 Series Layer 2 Gigabit Ethernet Managed Switch IP-MAC-Port Binding General Overview The Switch offers IP-MAC-Port Binding (IMPB), a D-Link security application used most often on edge switches directly connected to network hosts. IMPB is also an integral part of D-Link's End-to-End Security Solution (E2ES). The primary purpose of IP-MAC-Port Binding is to restrict client access to a switch by enabling administrators to configure pairs of client MAC and IP addresses that are allowed to access networks through a switch. Specifically, IMPB binds together the four-byte IP address and the six-byte Ethernet link layer MAC address to allow the transmission of data between the layers. The IMPB function is port-based, meaning that a user can enable or disable the function on any individual port. Once IMPB is enabled on a switch port, the switch will restrict or allow client access by checking the pair of IP-MAC addresses with the preconfigured database, also known as the "IMPB white list". If an unauthorized user tries to access an IMPB-enabled port, the system will block access by dropping its packet. The creation of the IMPB white list can be manually configured by CLI or Web. Common IP Management Security Issues Currently, certain limitations and issues in IP management structures can lead to serious security problems. Auditing mechanisms, such as syslog, application log, firewall log, etc, are mainly based on client IP information. However, such log information is meaningless if the client IP address can be easily changed. IP conflict, the most common problem in today's networks, is another major security concern. Without IMPB, any user can change an IP address manually and cause conflict with other resources, such as other PCs, core switches, routers or servers. Not only does this duplicate IP create an auditing issue, it also poses potential risk to the entire network. Auditing Problem 192.168.1.1 00E0-0211-1111 IP Conflict 192.168.1.2 00E0-0211-2222 192.168.1.1 00E0-0211-3333 IP Conflict Figure 6 - 5 Common IP Management IP Security Issues ARP spoofing attacks in which malicious users intercept traffic or interrupt connections by manipulating ARP packets are another serious challenge in securing today's network. Further information on how ARP spoofing attacks work can be found in the Appendix, "Mitigating ARP Spoofing Attack via Packet Content ACL," located in the back of this manual. Solutions to Improve IP Management Security D-Link has introduced IMPB technology to protect networks from attacks. By using IP-MAC-Port Binding, all packets are dropped by a switch when the combination of MAC address, IP address, and connected port is not in the IMPB white list. IMPB allows the user to choose either ARP or ACL mode. In addition, an IMPB white list can be dynamically created with the DHCP snooping option. DHCP snooping is a global setting and can be enabled on top of ACL or ARP mode. Each option has its advantages and disadvantages. ARP Mode In ARP Mode, a switch performs ARP Packet Inspection in which it checks the IP-MAC pairs in ARP packets with the IMPB white list and denies unauthorized ones. An advantage of ARP mode is that it does not consume any ACL rules on the Switch. Nonetheless, since the switch only checks ARP packets, it cannot block unauthorized clients who do not send out ARP packets. ACL Mode In ACL Mode, a switch performs IP Packet Inspection in addition to ARP Packet Inspection. Essentially, ACL rules will be used to permit statically configured IMPB entries and deny other IP packets with the incorrect IP-MAC pairs. The distinct advantage of ACL Mode is that it ensures better security by checking both ARP Packets and IP Packets. However, doing so requires the use of ACL rules. ACL Mode can be viewed as an enhanced version of ARP Mode because ARP Mode is enabled by default when ACL Mode is selected. 280