D-Link DGS-3426P Product Manual - Page 302
Guest VLANs, Limitations Using the Guest VLAN, 802.1X Port Settings
 |
UPC - 790069291982
View all D-Link DGS-3426P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 302 highlights
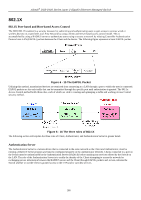
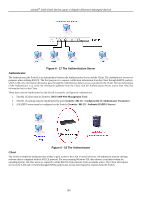
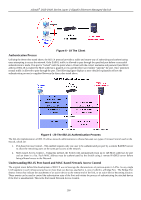
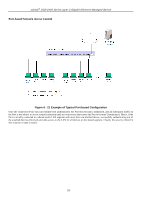
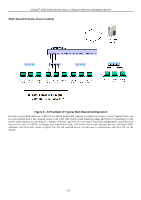
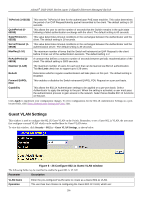
xStack® DGS-3400 Series Layer 2 Gigabit Ethernet Managed Switch Guest VLANs On 802.1X security enabled networks, there is a need for non 802.1X supported devices to gain limited access to the network, due to the lack of the proper 802.1X software or incompatible devices, such as computers running Windows 98 or lower operating systems, or the need for guests to gain access to the network without full authorization or local authentication on the Switch. To supplement these circumstances, this switch now implements Guest 802.1X VLANs. These VLANs should have limited access rights and features separate from other VLANs on the network. To implement Guest 802.1X VLANs, the user must first create a VLAN on the network with limited rights and then enable it as an 802.1X guest VLAN. Then the administrator must configure the guest accounts accessing the Switch to be placed in a Guest VLAN when trying to access the Switch. Upon initial entry to the Switch, the client wishing services on the Switch will need to be authenticated by a remote RADIUS Server or local authentication on the Switch to be placed in a fully operational VLAN. If authenticated and the authenticator posseses the VLAN placement information, that client will be accepted into the fully operational target VLAN and normal switch functions will be open to the client. If the authenticator does not have target VLAN placement information, the client will be returned to its originating VLAN. Yet, if the client is denied authentication by the has authenticator, limited rights it will be placed in the Guest VLAN and access. The adjacent figure should where it give the Figure 6 - 23 Guest VLAN Authentication Process user a better understanding of the Guest VLAN process. Limitations Using the Guest VLAN 1. Ports supporting Guest VLANs cannot be GVRP enabled and vice versa. 2. A port cannot be a member of a Guest VLAN and a static VLAN simultaneously. 3. Once a client has been accepted into the target VLAN, it can no longer access the Guest VLAN. 802.1X Port Settings This window is used to configure the 802.1X authenticator settings on the Switch. The user may toggle between switches in the switch stack by using the Unit pull-down menu. To view this window, click Security > 802.1X > 802.1X Port Settings, as shown below. 293