D-Link DGS-3426P Product Manual - Page 337
MAC-based Access Control Local MAC Settings
 |
UPC - 790069291982
View all D-Link DGS-3426P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 337 highlights
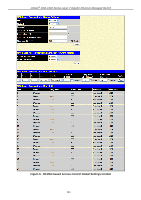
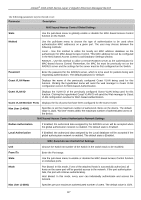
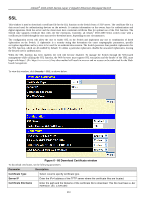
xStack® DGS-3400 Series Layer 2 Gigabit Ethernet Managed Switch Aging Time (1-1440 min) Specifies a time period (configurable per port) between 1-1440 minutes, during which an authenticated host will stay in an authenticated state. When the aging time has expired, the host will be moved back to an unauthenticated state. When aging time is set to Infinite, it will disable the aging time. Block Time (1-300sec) If a host fails to pass the authentication it will be blocked for a period of time referred to as block time (per port configurable). During this time, this host can't proceed to the authenticating process (unless the user clears the database manually). As a result, this hold mechanism can prevent the switch from frequent authentication which consumes too much computing power. Click Apply to implement changes made. MAC-based Access Control Local MAC Settings The following window is used to set a list of MAC addresses, along with their corresponding target VLAN, which will be authenticated for the Switch. Once a queried MAC address is matched in this table, it will be placed in the VLAN associated with it here. The switch administrator may enter up to 1024 MAC addresses to be authenticated using the local method configured here. To view this window, click Security > MAC-based Access Control > MAC-based Access Control Local MAC Settings, as shown below. Figure 6 - 59 MAC-based Access Control Local MAC Settings window To add a MAC address to the local authentication list, enter the MAC address and the target VLAN name into their appropriate fields and click Add. To clear a VLAN click Clear VLAN. To change a MAC address or a VLAN in the list, click the corresponding Modify button. To delete an entry by MAC or VLAN, enter its parameters into the appropriate field and click Delete By MAC or Delete By VLAN. To find an entry by MAC or VLAN, enter its parameters into the appropriate fields and click Find By MAC or Find By VLAN. Figure 6 - 60 MAC-based Access Control Local MAC Settings - Edit window 328