D-Link DGS-3426P Product Manual - Page 290
Strict and Loose State, DHCP Snooping Option, ARP Inspection, DHCP Snooping Example
 |
UPC - 790069291982
View all D-Link DGS-3426P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 290 highlights
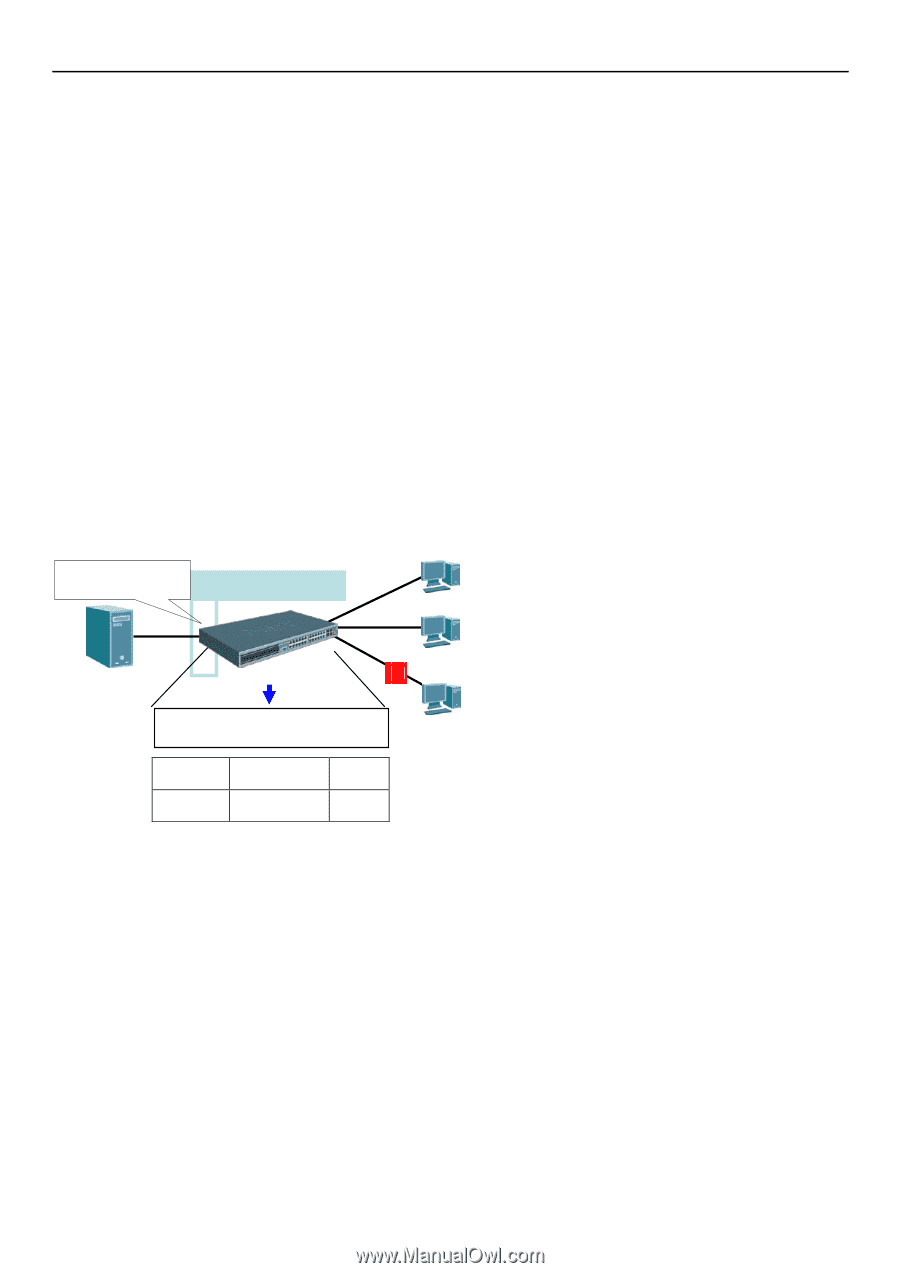
xStack® DGS-3400 Series Layer 2 Gigabit Ethernet Managed Switch Strict and Loose State Other than ACL and ARP mode, users can also configure the state on a port for granular control. There are two states: Strict and Loose, and only one state can be selected per port. If a port is set to Strict state, all packets entering the port are denied (dropped) by default. The switch will continuously compare all IP and ARP packets it receives on that port with its IMPB entries. If the IPMAC pair in the packet matches the IMPB entry, the MAC address will be unblocked and subsequent packets sent from this client will be forwarded. On the other hand, if a port is set to Loose state, all packets entering the port are permitted (forwarded) by default. The switch will continuously compare all ARP packets it receives on that port with its IMPB entries. If the IP-MAC pair in the ARP packet does not match the IMPB white list, the MAC address will be blocked and subsequent packets sent from this client will be dropped. DHCP Snooping Option If DHCP snooping is enabled, the switch learns IP-MAC pairs by snooping DHCP packets automatically and then saves them to the IP-MAC-Port Binding white list. This enables a hassle-free configuration because the administrator does not need to manually enter each IMPB entry. A prerequisite for this is that the valid DHCP server's IP-MAC pair must be configured on the switch's IMPB while list first; otherwise the DHCP server packets will be dropped. DHCP snooping is generally considered to be more secure because it enforces all clients to acquire IP through the DHCP server. Additionally, it makes IP Information auditable because clients cannot manually configure their own IP address. An example of DHCP snooping in which PC-A and PC-B get their IP addresses from a DHCP server is depicted below. The switch snoops the DHCP conversation between PC-A, PC-B, and the DHCP server. The IP address, MAC address, and connecting ports of both PC-A and PC-B are learned and stored in the switch's IMPB white list. Therefore, these PCs will be able to connect to the network. Then there is PC-C, whose IP address is manually configured by the user. Since this PC's IP-MAC pair does not match the one on Switch's IMPB white list, traffic from PC-C will be blocked. Doesn't match the White list, block PC-C IMP Binding Enabled DHCP Server Address Learning White List PC-A PC-B 192.168.1.1 00E0-0211-1111 192.168.1.2 00E0-0211-2222 (IP assigned by DHCP for PC-A and PC-B) PC-C 192.168.1.1 00E0-0211-3333 (IP manually configured by user) 192.168.1.1 00E0-0211-111 Port 1 192.168.1.2 00E0-0211-222 Port 2 ARP Inspection Figure 6 - 6 DHCP Snooping Example ARP spoofing can attack hosts, switches, and routers connected to a Layer 2 network by "poisoning" their ARP caches. As the figure below shows, Host C can "poison" the ARP caches of Host B by broadcasting forged ARP responses with bindings (IP B, MAC C). As a result, Host C intercepts the traffic sent to Host B. IMPB v3.8 was developed to prevent this kind of ARP spoofing (including Netcut and Netcut restore attacks). 281