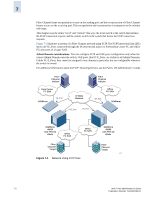
HP StorageWorks 2/16V Brocade Web Tools Administrator's Guide (53-0000194-01, - Page 115
Limitations, Unsupported with IKE/IPSec, NAT Traversal
 |
View all HP StorageWorks 2/16V manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 115 highlights
7 IPSec helps provide in-depth defense against: • Network-based attacks from untrusted computers, which can result in the denial-of-service of applications, services, or the network • Data corruption • Data theft • User-credential theft • Administrative control of servers, other computers, and the network Limitations Consider the following limitations if you plan to use IPSec: • Policies cannot be altered. To change the parameters associated with a current IKE or IPSec policy, that policy must be deleted and re-created with the altered parameters. • A policy cannot be deleted while an active FCIP tunnel is using it. • As with other FCIP tunnel configuration parameters, IPSec configuration on both ends of the tunnel must match for the tunnel to be established. (IPSec is an optional feature and is not required to be enabled.) • If IPSec is to be enabled on an FCIP tunnel, you must specify the preshared key, IKE, and IPSec policy numbers. • Only a single secure tunnel is allowed on a port. Nonsecure tunnels are not allowed on the same port as secure tunnels. • Fastwrite and tape pipelining are not supported with secure tunnels. • Modify operations are not allowed on secure tunnels. To change the configuration of a secure tunnel, first delete the tunnel and then re-create it with the desired options. • Jumbo frames are not supported on secure tunnels. • Only a single route is supported on an interface with a secure tunnel. Unsupported with IKE/IPSec The following implementations are currently not supported with IKE/IPSec: • IPV6 • ESP in transport mode • NAT Traversal Web Tools Administrator's Guide 7-5 Publication Number: 53-0000194-01