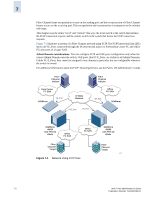
HP StorageWorks 2/16V Brocade Web Tools Administrator's Guide (53-0000194-01, - Page 116
Table 7-2, Field, Description, Choices, Perfect Forward Secrecy - transformer
 |
View all HP StorageWorks 2/16V manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 116 highlights
7 Table 7-2 explains the fields and related choices to create an IKE/IPSec policy. Table 7-2 IKE/IPSec Configuration Choices Field Description Choices Policy Type You can create either an IKE policy or an IPSec IKE policy IPSec Policy Number This parameter helps you keep track of the number of policies you have created on your switch. You can choose any number from 1 through 32. You can define up to 32 IKE and 32 IPSec policies per switch. 1 through 32 Encryption Algorithm A mathematical procedure for performing encryption on data. Through the use of an algorithm, information is made into meaningless cipher text and requires the use of a key to transform the data back into its original form. 3DES AES-128 AES-256 Authentication Algorithm An encryption process or tool in which the results SHA-1 of text encryption depend on all relevant MD5 authentication elements. AES-XCBC Perfect Forward Secrecy (PFS) In an authenticated key agreement protocol that uses public key cryptography, PFS is the property of disclosure of the long-term secret keying material that is used to derive an agreed ephemeral key that does not compromise the secrecy of the agreed keys from earlier runs. IKE on/off IPSec disabled Diffie-Hellman (D-H) Diffie-Hellman key exchange is a cryptographic protocol that allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure communications channel. This key can then be used to encrypt subsequent communications using a symmetric key cipher IKE 1 or 14 IPSec disabled Security Association Lifetime This specifies the lifetime in seconds of the security association and a new key will be renegotiated before this value expires if PFS is on. The security association will expire when either this value or the value lifetime is reached. Specify the number of seconds 7-6 Web Tools Administrator's Guide Publication Number: 53-0000194-01