D-Link DWC-1000 User Manual - Page 223
Protecting from Internet Attacks
 |
View all D-Link DWC-1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 223 highlights
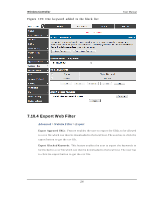
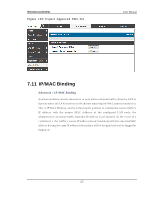
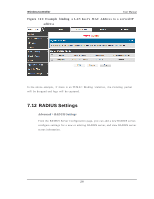
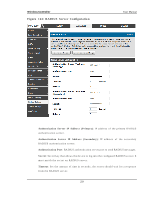
Wireless Controller User Manual p o rt is co n n ect ed is les s t h an wh en all o f t h e av ailab le LA N p o rt s h a v e an act iv e Et h ern et co n n ect io n . Leng th Detecti on S tate: W h en en ab led t h e LA N co n t ro ller will red u ce t h e o v erall cu rren t s u pplied t o t he LA N p o rt wh en a s mall cab le len g t h is co nn ected t o t h at p o rt . Lo n g er cab les h ave h ig her resis tance t h an s h o rt er ca b les an d req u ire mo re p o wer t o t ran s mit p acket s o ver t h at d ist an ce. Th is o p t io n will red u ce t h e p o wer t o a LA N p o rt if an Et h ern et cab le o f les s t h an 10 ft is d et ect ed as b ein g co n n ect ed t o t h at p o rt . J umbo Frames Opti on: W h en en ab led , LA N s id e d ev ices can exch an g e t raffic co n t an in g ju mb o frames . 7.14 Protecting from Internet Attacks Advanced > Advanced Network > Attack Checks A t t acks can b e malicio u s s ecu rit y b reach es o r u n in t en t io n al n et wo rk is s u es t h at ren d er t h e co n troller u n u sab le. A tt ack ch ecks allo w y o u t o man ag e Op t io n s ecu rit y threats s uch as continual ping requests and dis covery via A RP s cans . TCP and UDP flo o d at t ack ch ecks can b e en ab led t o man ag e ext reme u s ag e o f Op t io n res o u rces . A dditionally certain Denial-of-Service (DoS) attacks can be blocked. These attacks , if uninhibited, can us e up proces s ing power and bandwidth and prevent regular n et wo rk s erv ices fro m ru n n in g n o rmally . ICM P p acket flo o d in g , SYN t raffic flo o d in g , an d Ech o s torm t h res ho lds can b e con fig ured t o t emp orarily s usp ect t raffic from the offending s ource. 221