D-Link DWC-1000 User Manual - Page 292
Known Client Database RADIUS Server Name
 |
View all D-Link DWC-1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 292 highlights
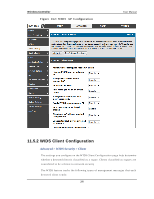
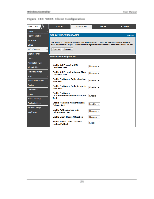
Wireless Controller User Manual Known Cl i ent Databas e Look up Method: W h en t h e co n t ro ller d et ect s a clien t o n t h e n et wo rk it p erfo rms a lo o ku p in t h e Kn o wn Clien t d at ab as e. Sp ecify wh et h er the controller s hould us e the local or RADIUS databas e for thes e lookups . Known Cl i ent Databas e RADIUS S erver Name : If t h e kn o wn clien t d at ab as e lo o ku p met h o d is RA DIUS t h en t h is field s p e cifies t h e RA DIUS s erv er n ame. Rog ue Detected Trap Interval : Sp ecify t h e in t erv al, in s eco n d s , b et ween t ran s mis sio ns o f t h e SNM P t rap t ellin g t h e admin is t rator t h at ro g ue A Ps are p resent in the RF Scan databas e. If you s et the value to 0, the trap is never s ent. De-Authenti cati on Reques ts Thres hol d Interval : Sp ecify t h e n u mb er o f s eco n d s an A P s h o u ld s p en d co u n t in g t h e DE au t h en t icat io n mes s ag es s en t b y wireles s clients . De-Authenti cati on Reques ts Thres hol d Val ue: If co n t ro ller receiv es mo re t h an s p ecified mes s ag es d u rin g t h e t h res h o ld in t erv al t h e t es t t rig g ers . Authenti cati on Reques ts Thres hol d Interval : Sp ecify t h e n u mb er o f s eco n d s an A P s h o u ld s pen d co u n t in g t h e au t h en t icat io n mes s ag es s en t b y wireles s clien t s . Authenti cati on Reques ts Thres hol d Val ue : If co n t ro ller receiv es mo re t h an s p ecified mes s ages d u ring t he t h resh old in t erv al t h e t es t t rig g ers . Pro b e Req u es t s Th res h old In t erval Sp ecify t h e n umb er o f s econ ds an A P s ho uld sp en d co un tin g t h e p ro b e mes s ag es s en t b y wireles s clien t s . Probe Reques ts Thre s hol d Val ue : Sp ecify t h e n u mb er o f p ro b e req u ests a wireless client is allowed to s end during the threshold interval before the event is reported as a threat. Authenti cati on Fai l ure Thres hol d Val ue : Sp ecify t h e n u mb er o f 802.1X authentication failures a client is allowed to have before the event is reported as a threat. 290