D-Link DWC-1000 User Manual - Page 304
useful when the Default Outbound Policy is Block Always so the IT admin can, Outbound Policy is
 |
View all D-Link DWC-1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 304 highlights
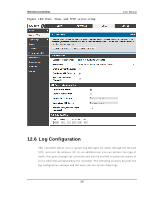
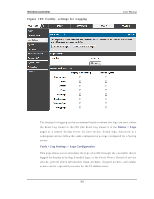
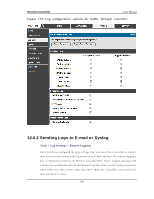
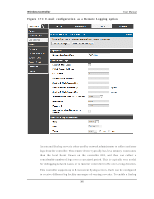
Wireless Controller User Manual Traffic t h ro u g h each n etwo rk s egmen t (LA N, Op t io n , DM Z) can b e t racked b ased on whether the packet was accepted or dropp ed by the firewall. Accepted Packets are thos e that were s ucces s fully trans ferred through the co rres p o n d in g n et wo rk s eg men t (i.e. LA N t o Op t io n ). Th is o p t io n is p art icu larly u s efu l wh en t h e Defau lt Ou t b o u n d Po licy is "Blo ck A lway s " s o t h e IT ad min can mo n it o r t raffic t h at is p as s ed t h ro u g h t h e firewall. Exampl e : If A ccep t Packet s fro m LA N t o Op t io n is en ab led an d t h ere is a firewall ru le t o allo w SSH t raffic fro m LA N, t h en wh en ev er a LA N mach in e t ries t o make an SSH co n n ect io n , t h o s e p acket s will b e accep t ed an d a mes s ag e will b e lo g g ed . (A s s u min g t h e lo g o p t io n is s et t o A llo w fo r t h e SSH firewall rule.) Dropped Packets are packets that were intentionally blocked from being trans ferred t h ro u g h t h e co rrespo ndin g n et work s eg men t. Th is o p tio n is u s efu l wh en t h e Defau lt Outbound Policy is "Allow Always ". Exampl e : If Dro p Packet s fro m LA N t o Op t io n is en ab led an d t h ere is a firewall ru le t o b lo ck SSH t raffic fro m LA N, t h en wh en ev er a LA N mach in e t ries t o make an SSH co n n ect io n , t h o s e p acket s will b e d ro p p ed a n d a mes s ag e will b e lo g g ed . (M ake s u re t h e lo g o p t io n is s et t o allo w fo r t h is firewall rule.) En ab lin g accep t ed p acket lo g g in g t h ro u g h t h e firewall may g en erat e a s ig n ifican t v o lu me o f lo g mes s ag es d ep en d in g o n t h e t y p ical n et wo rk t raffic. Th is is reco mmen d ed fo r d eb u g g in g p u rp o s es o n ly . In ad d it io n t o n et work s egmen t lo g gin g, u n icast an d mu lt icast t raffic can b e lo g g ed . Unicas t packets have a s ingle des tination on the network, whereas broadcas t (or mu lt icas t ) p acket s are s en t t o all p o s s ib le d es t in at io n s s imu lt an eo u s ly . On e o t h er us eful log control is to log packets that are dropped due to configured bandwidth p ro files o v er a p art icu lar in t erface. Th is d ata will in d icat e t o t h e ad min wh et h er t h e b an d wid t h p ro file h as t o b e mo d ified t o acco u n t fo r t h e d es ired in t ern et t raffic o f LA N u s ers . 302