D-Link DWC-1000 User Manual - Page 235
Configuring VPN clients
 |
View all D-Link DWC-1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 235 highlights
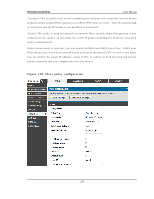
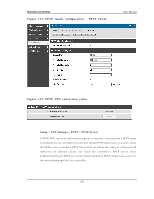
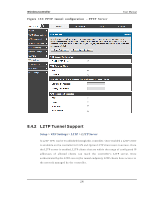
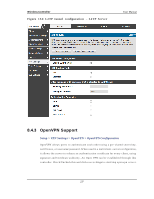
Wireless Controller User Manual W ith a configured RA DIUS s erver, the controller connects to a RA DIUS s erver and p as s es t o it t h e credent ials t h at it receiv es fro m t h e VPN clien t . Yo u can s ecu re t h e connection between the controller and the RADIUS s erver with the authentication protocol s upported by the s erver (PAP or CHAP). For RADIUS - PAP, the controller firs t checks in the us er databas e to s ee if the us er credentials are available; if they are not, the controller connects to the RADIUS s erver. 8.2.2 Internet ov er IPSec tunnel In t h is feat u re all t h e t raffic will p as s t h rou gh t h e VPN Tu n n el an d fro m t h e Rem o t e Gat eway t h e p acket will b e ro u t ed t o In t ern et . On t h e remo t e g at eway s id e, t h e outgoing packet will be SNAT'ed. 8.3 Configuring VPN clients Remo t e VPN clien t s mu s t b e co nfig u red wit h t h e s ame VPN p o licy p aramet ers used in t h e VPN t u n n el t h at t h e clien t wis h es t o u se: en crypt io n, au thent icat ion , life t ime, an d PFS key -g ro u p . Up o n es t ab lis h in g t h es e au t h en t icat io n p aramet ers , t h e VPN Clien t u s er d at ab as e mu s t als o b e p o p u lat ed wit h an acco u n t t o g iv e a u s er acces s t o t h e t u n n e l. VPN clien t s o ft ware is req u ired t o es t ab lis h a VPN t u n n el b et ween t h e co n t ro ller an d remo t e en dpo int . Op en s o urce s oft ware (su ch as Op en VPN or Op en s wan ) as well as M icro s o ft IPs ec VPN s o ft ware can b e co n fig u red wit h t h e req u ired IKE p o licy p aramet ers t o es t ab lis h an IPs ec VPN t u n n e l. Refer to the client s oftware guide for detailed ins tructions on s etup as well as the controller‟s online help. Th e u s er d at abase co nt ain s t he lis t o f VPN u s er acco un ts t h at are au t h o rized t o u s e a g iv en VPN t u n n el. A lt ern at iv ely VPN t u n n el u s ers can b e au t h en t icat ed u s in g a co n fig u red Rad iu s d at ab ase. Refer t o t h e o nlin e h elp t o d et ermin e h o w t o p o pu late the us er databas e and/or configure RADIUS authentication. 233