Netgear GS724TPv2 User Manual - Page 202
Con Port Authentication, Rule Type, Permit, Service Type, Secure HTTP SSL, Source IP Address
 |
View all Netgear GS724TPv2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 202 highlights
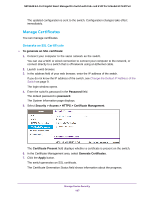
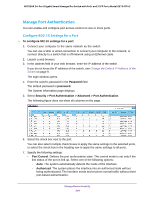
NETGEAR 24-Port Gigabit Smart Managed Pro Switch with PoE+ and 2 SFP Ports Model GS724TPv2 6. From the Rule Type menu, select Permit or Deny to permit or deny access when the selected rules are matched. A Permit rule allows access by traffic that matches the rule criteria. A Deny rule blocks traffic that matches the rule criteria. 7. From the Service Type menu, select the access method to which the rule is applied. The policy is restricted by the selected access method. Possible access methods are HTTP, Secure HTTP (SSL), and SNMP. 8. In the Source IP Address field, enter the source IP address of the client originating the management traffic. 9. In the Mask field, specify the subnet mask of the client that originates the management traffic. 10. In the Priority field, assign a priority to the rule. The rules are validated against the incoming management request in ascending order of their priorities. If a rule matches, the action is performed and subsequent rules below that are ignored. For example, if a source IP 10.10.10.10 is configured with priority 1 to permit, and source IP 10.10.10.10 is configured with priority 2 to deny, then access is permitted if the profile is active, and the second rule is ignored. 11. Click the Add button. The access rule is added. Configure Port Authentication With port-based authentication, when 802.1X is enabled globally and on the port, successful authentication of any one supplicant attached to the port results in all users being able to use the port without restrictions. At any given time, only one supplicant is allowed to attempt authentication on a port in this mode. Ports in this mode are under bidirectional control. This is the default authentication mode. An 802.1X network includes three components: • Authenticators. The port that is authenticated before system access is permitted. • Supplicants. The host connected to the authenticated port requesting access to the system services. • Authentication Server. The external server, for example, the RADIUS server that performs the authentication on behalf of the authenticator, and indicates whether the user is authorized to access system services. Manage Device Security 202