Konica Minolta bizhub C280 Product Guide - Page 176
Copy Guard, Password Copy, Authentication For User Box Access, Limiting Access To Destinations
 |
View all Konica Minolta bizhub C280 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 176 highlights
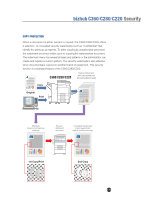
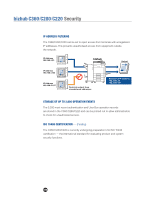
bizhub C360/C280/C220 Security COPY GUARD* The Copy Guard feature detects the predetermined background pattern on the unauthorized copy and completely prohibits copying. PASSWORD COPY* Although the predetermined background pattern on the unauthorized copy is detected, copies are allowed via a password. *Requires an optional Security Kit SC-507 AUTHENTICATION FOR USER BOX ACCESS The correct four-digit password must be entered to access data in a User Box. The password must also be entered on the control panel to send data stored in a private User Box by Email or FTP directly from the C360/C280/C220. The Administrator Password must be entered to back up data from a User Box onto a PC or to restore data in a User Box from a PC.* *HDD Backup Utility is required. LIMITING ACCESS TO DESTINATIONS Limits can be placed on the destinations that appear for each user that is accessing them. This function allows a group and level to be specified for the address book destination and settings to be specified for applying limits to registered destinations. An access permission level can be specified for each user and destination. The destinations that can be accessed by users can be limited according to the access permission levels specified for the user and destination. 172