Cisco N7K-C7010 Configuration Guide - Page 212
Features That You Must Manually Con on the Primary and Secondary Devices, vPC Peer Links and STP
 |
UPC - 882658174445
View all Cisco N7K-C7010 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 212 highlights
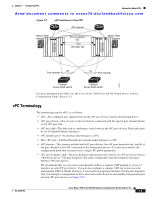
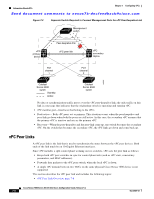
Information About vPCs Chapter 7 Configuring vPCs Send document comments to [email protected] Note We recommend that you use two different modules for redundant on each vPC peer device vPC peer links. The software keeps all traffic that forwards across the vPC peer devices as local traffic. A packet that ingresses the port channel uses one of the local links rather than moving across the vPC peer link. Unknown unicast, multicast, and broadcast traffic (including STP BPDUs) are flooded across the vPC peer link. The software keeps the multicast forwarding state synchronized on both of the vPC peer devices. You can configure any of the standard load-balancing schemes on both the vPC peer link devices and the downstream device (see Chapter 6, "Configuring Port Channels," for information on load balancing). Configuration information flows across the vPC peer links using the Cisco Fabric Service over Ethernet (CFSoE) protocol. (See the "CFSoE" section on page 7-26 for more information about CFSoE.) All MAC addresses for those VLANs configured on both devices are synchronized between vPC peer devices. The software uses CFSoE for this synchronization. (See the "CFSoE" section on page 7-26 for information about CFSoE.) If the vPC peer link fails, the software checks the status of the remote vPC peer device using the peer-keepalive link, which is a link between vPC peer devices that ensures that both devices are up. If the vPC peer device is up, the secondary vPC device disables all vPC ports on its device, to prevent loops and disappearing or flooding traffic. The data then forwards down the remaining active links of the port channel. Note We recommend that you create and configure a separate VRF and configure a Layer 3 port on each vPC peer device in that VRF for the vPC peer-keepalive link. The default ports and VRF for the peer-keepalive are the management ports and VRF. The software learns of a vPC peer device failure when the keepalive messages are not returned over the peer-keepalive link. Use a separate link (vPC peer-keepalive link) to send configurable keepalive messages between the vPC peer devices. The keepalive messages on the vPC peer-keepalive link determines whether a failure is on the vPC peer link only or on the vPC peer device. The keepalive messages are used only when all the links in the peer link fail. See the "Peer-Keepalive Link and Messages" section on page 7-11 for information about the keepalive message. Features That You Must Manually Configure on the Primary and Secondary Devices You must manually configure the following features to conform to the primary/secondary mapping of each of the vPC peer devices: • STP root-Configure the primary vPC peer device as the STP primary root device and configure the vPC secondary device to be the STP secondary root device. See the "vPC Peer Links and STP" section on page 7-21 for more information on vPC and STP. - We recommend that you configure the vPC peer link interfaces as STP network ports so that Bridge Assurance is enabled on all vPC peer links - We recommend that you configure Rapid PVST+ so that the primary device is the root for all VLANs and configure MST so that the primary device is the root for all instances. • Layer 3 VLAN network interface-Configure Layer 3 connectivity from each vPC peer device by configuring a VLAN network interface for the same VLAN from both devices. 7-10 Cisco Nexus 7000 Series NX-OS Interfaces Configuration Guide, Release 5.x OL-23435-03