Netgear GS752TS GS7xxTS-TPS Software Admin Manual - Page 207
Authentication List Configuration, admin, Security, Management Security >, Authentication List
 |
View all Netgear GS752TS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 207 highlights
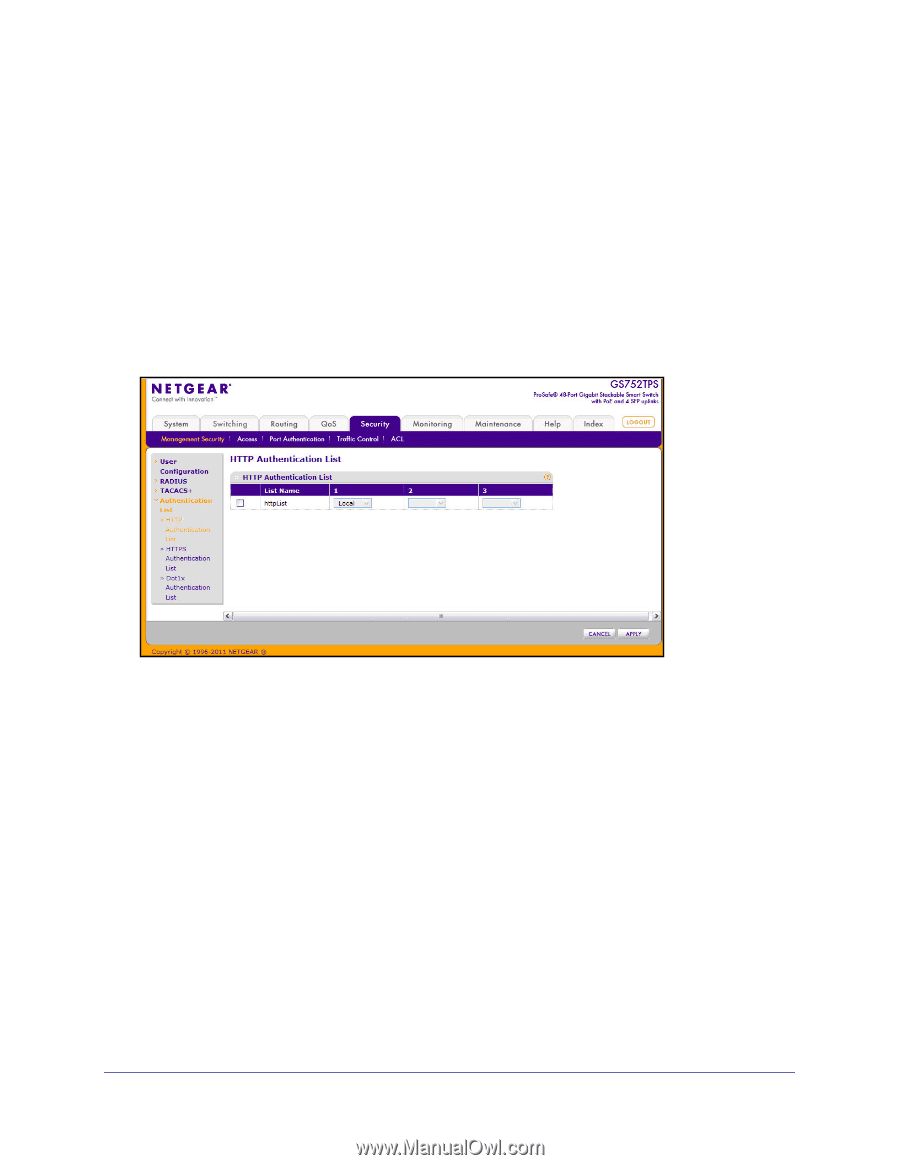
GS728TS, GS728TPS, GS752TS, and GS752TPS Gigabit Smart Switches Authentication List Configuration From the Authentication List pages, you can configure the login lists for HTTP, HTTPS, or IEEE 802.1X authentication. A login list specifies one or more authentication methods to validate switch or port access. HTTP Authentication List Use the HTTP Authentication List page to configure the authentication method(s) the admin user must use when accessing the management interface through HTTP. To access the HTTP Authentication List page, click Security > Management Security > Authentication List, and then click the HTTP Authentication List link. To change the authentication method for the httpList: 1. Select the check box next to the httpList name 2. Use the drop down menu in the 1 column to select the authentication method that should appear first in the selected authentication login list. If you select a method that does not time out as the first method, such as 'local', no other method will be tried, even if you have specified more than one method. This parameter will not appear when you first create a new login list. User authentication occurs in the order the methods are selected. Possible methods are as follows: • Local: The user's locally stored ID and password will be used for authentication. Since the local method does not time out, if you select this option as the first method, no other method will be tried, even if you have specified more than one method. • RADIUS: The user's ID and password will be authenticated using the RADIUS server. If you select RADIUS or TACACS+ as the first method and an error occurs during the authentication, the switch uses Method 2 to authenticate the user. • TACACS+: The user's ID and password will be authenticated using the TACACS+ server. If you select RADIUS or TACACS+ as the first method and an error occurs during the authentication, the switch attempts user authentication Method 2. • None: The authentication method is unspecified. 207