Netgear GS752TS GS7xxTS-TPS Software Admin Manual - Page 92
Services — DHCP Snooping, DHCP Snooping Global Configuration, Interface Configuration
 |
View all Netgear GS752TS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 92 highlights
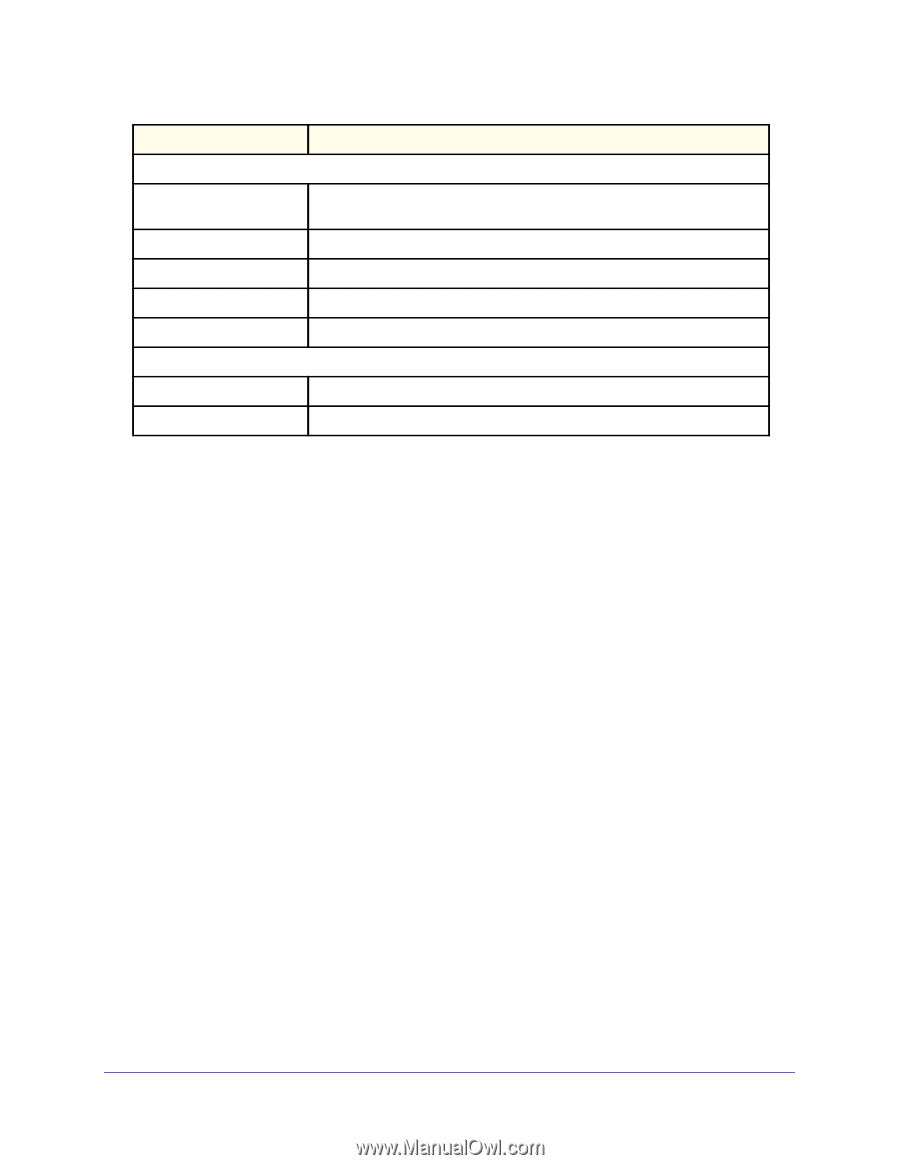
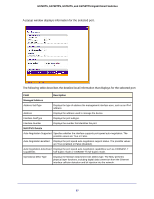
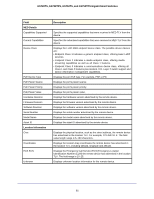
GS728TS, GS728TPS, GS752TS, and GS752TPS Gigabit Smart Switches Field Network Policies Application Type VLAN ID VLAN Type User Priority DSCP LLDP Unknown TLVs Type Value Description Specifies the media application type associated with the policy advertised by the remote device. Specifies the VLAN ID associated with the policy. Specifies whether the VLAN associated with the policy is tagged or untagged. Specifies the priority associated with the policy. Specifies the DSCP associated with a particular policy type. Displays the unknown TLV type field. Displays the unknown TLV value field. Services - DHCP Snooping DHCP Snooping is a useful feature that provides security by filtering untrusted DHCP messages and by building and maintaining a DHCP snooping binding table. An untrusted message is a message that is received from outside the network or firewall and that can cause traffic attacks within your network. A known attack is when an unauthorized DHCP server responds to a client that is requesting an IP address. The server configures the gateway for the client to be equal to the IP address of the server. At that point, the client sends all of its IP traffic destined to other networks to the unauthorized machine. This gives the attacker the possibility of snooping traffic for passwords or employing a man-in-the-middle attack. The DHCP snooping binding table contains the MAC address, IP address, lease time, binding type, VLAN number, and interface information that corresponds to the local untrusted interfaces of a switch. An untrusted interface is an interface that is configured to receive messages from outside the network or firewall. A trusted interface is an interface that is configured to receive only messages from within the network. DHCP snooping acts like a firewall between untrusted hosts and DHCP servers. It also provides way to differentiate between untrusted interfaces connected to the end-user and trusted interfaces connected to the DHCP server or another switch. From the Services link, you can access the following pages: • DHCP Snooping Global Configuration on page 93 • Interface Configuration on page 94 • Binding Configuration on page 95 • Persistent Configuration on page 97 • Statistics on page 98 92