Netgear GS752TS GS7xxTS-TPS Software Admin Manual - Page 94
Interface Configuration, System, Services, DHCP Snooping, Trust Mode, Enable, Disable
 |
View all Netgear GS752TS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 94 highlights
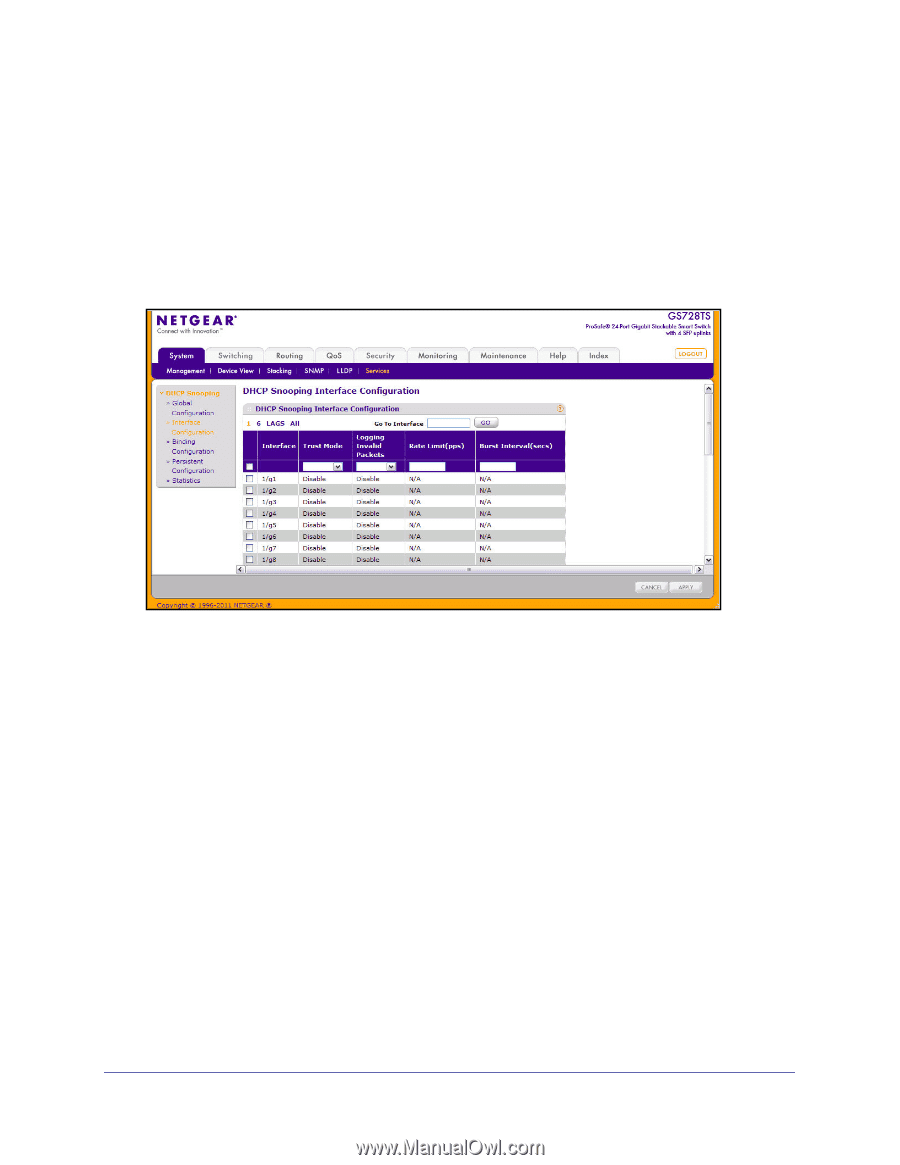
GS728TS, GS728TPS, GS752TS, and GS752TPS Gigabit Smart Switches Interface Configuration Use the DHCP Snooping Interface Configuration page to view and configure each port or LAG as trusted or untrusted. Any DHCP responses received on a trusted port are forwarded. If a port is configured as untrusted, any DHCP (or BootP) responses received on that port are discarded. To access the DHCP Snooping Interface Configuration page, click System> Services > DHCP Snooping > Interface Configuration. To configure DHCP snooping settings for an interface: 1. To configure DHCP snooping settings for a physical port, click the unit ID of the stack member with the ports to configure. 2. To configure DHCP snooping settings for a Link Aggregation Group (LAG), click LAGS. 3. To configure DHCP snooping settings for both physical ports and LAGs, click ALL. 4. Select the check box next to the port or LAG to configure. You can select multiple ports and LAGs to apply the same setting to the selected interfaces. Select the check box in the heading row to apply the same settings to all interfaces. 5. Choose the Trust Mode for the selected port(s) or LAG(s). • Enable: Any DHCP responses received on this port are forwarded. The port connected downstream from the authorized DHCP server should be configured as a trusted port. Any DHCP responses received on a trusted port are forwarded. All other ports should be configured as untrusted. Any DHCP (or BootP) responses received are discarded. • Disable: Any DHCP (or BootP) responses received on this port are discarded. Ports connected to hosts should be configured as untrusted. This is the default value. 6. Use the Logging Invalid Packets menu to choose whether to log invalid packets. When enabled, the DHCP snooping application sends a log message to the buffered log to record invalid packets received on this interface. The factory default is disabled. 94