Dell Powerconnect W-ClearPass Virtual Appliances W-ClearPass Guest 6.0 Deploym - Page 23
Security Policy Considerations, AirGroup Deployment Process
 |
View all Dell Powerconnect W-ClearPass Virtual Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 23 highlights
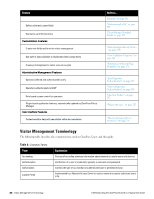
Security Policy Considerations To ensure that your network remains secure, decisions have to be made regarding guest access: l Do you wish to segregate guest access? Do you want a different VLAN, or different physical network infrastructure to be used by your guests? l What resources are you going to make available to guests (for example, type of network access; permitted times of day; bandwidth allocation)? l Will guest access be separated into different roles? If so, what roles are needed? l How will you prioritize traffic on the network to differentiate quality of service for guest accounts and non-guest accounts? l What will be the password format for guest accounts? Will you be changing this format on a regular basis? l What requirements will you place on the shared secret, between NAS and the RADIUS server to ensure network security is not compromised? l What IP address ranges will operators be using to access the server? l Should HTTPS be required in order to access the visitor management server? AirGroup Deployment Process AirGroup allows users to register their personal mobile devices on the local network and define a group of friends or associates who are allowed to share them. You use ClearPass Guest to define AirGroup administrators and operators. AirGroup administrators can then use ClearPass Guest to register and manage an organization's shared devices and configure access according to username, role, or location. AirGroup operators (end users) can use ClearPass Guest to register their personal devices and define the group who can share them. Table 5 summarizes the steps for configuring AirGroup functionality in ClearPass Guest. Details for these steps are provided in the relevant sections of this Guide. This table does not include the configuration steps performed in ClearPass Policy Manager or the W-Series controller. For complete AirGroup deployment information, refer to the AirGroup Deployment Guide and the ClearPass Policy Manager documentation. Table 5: Summary of AirGroup Configuration Steps in ClearPass Guest Step Section in this Guide Create AirGroup administrators "Creating a New Operator" on page 248 Create AirGroup operators "Creating a New Operator" on page 248 Configure an operator's device limit "Configuring AirGroup Operator Device Limit " on page 247 To authenticate AirGroup users via LDAP: l Define the LDAP server l Define appropriate translation rules "External Operator Authentication" on page 248 "LDAP Translation Rules " on page 254 AirGroup administrator: Register devices or groups of devices "AirGroup Device Registration " on page 53 AirGroup operator: Register personal devices "AirGroup Device Registration " on page 53 (Optional) Configure device registration form with dropdown lists for existing locations and roles "Customizing AirGroup Registration Forms " on page 147 Dell Networking W-ClearPass Guest 6.0 | Deployment Guide Security Policy Considerations | 23