Dell Powerconnect W-ClearPass Virtual Appliances W-ClearPass Guest 6.0 Deploym - Page 76
Devices Supporting Onboard Provisioning,
 |
View all Dell Powerconnect W-ClearPass Virtual Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 76 highlights
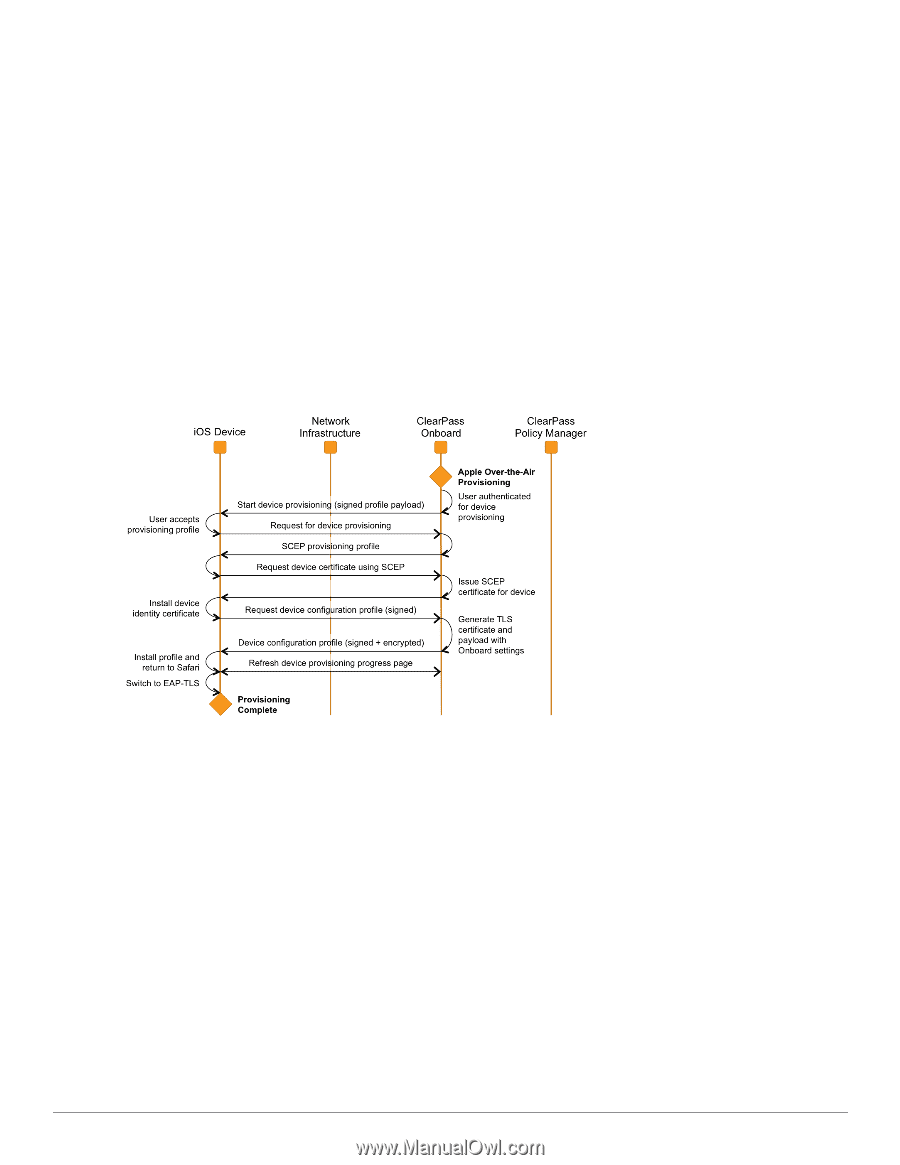
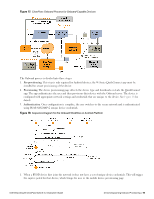
1. When a BYOD device first joins the provisioning network it does not have a set of unique device credentials. This will trigger the captive portal for that device, which brings the user to the mobile device provisioning page. 2. A link on the mobile device provisioning page prompts the user to install the enterprise's root certificate. Installing the enterprise's root certificate enables the user to establish the authenticity of the provisioning server during device provisioning. 3. The user then authenticates with their provisioning credentials - these are typically the user's enterprise credentials from Active Directory. If the user is authorized to provision a mobile device, the over-the-air provisioning workflow is then triggered (see Figure 16, below). 4. After provisioning has completed, the device switches to EAP-TLS authentication using the newly provisioned client certificate. Mutual authentication is performed (the authentication server verifies the client certificate, and the client verifies the authentication server's certificate). 5. The device is now onboard and is able to securely access the provisioned network. Over-the-air provisioning is used to securely provision a device and configure it with network settings. Figure 16 shows a sequence diagram that explains the steps involved in this workflow. Figure 16: Over-the-Air Provisioning Workflow for iOS Platform 1. The only user interaction required is to accept the provisioning profile. This profile is signed by the Onboard server, so that the user can be assured of its authenticity. 2. An iOS device will have two certificates after over-the-air provisioning is complete: a. A Simple Certificate Enrollment Protocol (SCEP) certificate is issued to the device during the provisioning process. This certificate identifies the device uniquely, and is used to encrypt the device configuration profile so that only this device can read its unique settings. b. A Transport Layer Security (TLS) client certificate is issued to the device. This certificate identifies the device and the user that provisioned the device. It is used as the device's network identity during EAP-TLS authentication. Devices Supporting Onboard Provisioning Dell Networking W-ClearPass Onboard supports secure device provisioning for Microsoft Windows XP (service pack 3 and later), Microsoft Windows Vista, Microsoft Windows 7, Apple Mac OS X 10.5 and 10.6, and Android devices (smartphones and tablets). These are collectively referred to as "Onboard-capable devices". The Onboard process for these devices is shown in Figure 17. 76 | Devices Supporting Onboard Provisioning Dell Networking W-ClearPass Guest 6.0 | Deployment Guide