Dell Powerconnect W-ClearPass Virtual Appliances W-ClearPass Guest 6.0 Deploym - Page 70
Certificate Configuration in a Cluster, Revoking Unique Device Credentials
 |
View all Dell Powerconnect W-ClearPass Virtual Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 70 highlights
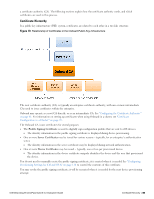
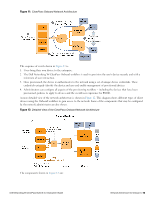
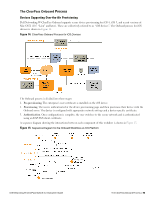
Certificate Configuration in a Cluster When you use Onboard in a cluster, you must use one common root certificate authority (CA) to issue all CPPM server certificates for the cluster. This allows the "verified" message in iOS and lets you verify that the CPPM server certificate is valid during EAP-PEAP or EAP-TLS authentication. In a cluster of CPPM servers, devices can be onboarded through any node or authenticated through any node. Each CPPM server has a different certificate, used for both SSL and RADIUS server identity. In the default configuration, these are self-signed certificates-that is, they are not issued by a root CA. This configuration of multiple self-signed certificates will not work for Onboard: Although a single self-signed certificate can be trusted, multiple self-signed certificates are not. There are two ways to configure a common root CA to issue all the CPPM server certificates for a cluster: l Use the Onboard certificate authority. Create a certificate signing request on each CPPM node, sign the certificates using Onboard, and install them in CPPM. You can then onboard devices on any node in the cluster, and can perform secure EAP authentication from a provisioned device to any node in the cluster. l Use a commercial certificate authority to issue CPPM server certificates. Verify that the same root CA is at the top of the trust chain for every server certificate, and that it is the trusted root certificate for Onboard. Provisioning and authentication will then work across the entire cluster. Revoking Unique Device Credentials Because each provisioned device uses unique credentials to access the network, it is possible to disable network access for an individual device. This offers a greater degree of control than traditional user-based authentication - disabling a user's account would impact all devices using those credentials. To disable network access for a device, revoke the TLS client certificate provisioned to the device. See "Working with Certificates in the List " on page 97. NOTE: Revoking access for a device is only possible when using an enterprise network. Personal (PSK) networks do not support this capability. Revoking Credentials to Prevent Network Access NOTE: Revoking a device's certificate will also prevent the device from being re-provisioned. This is necessary to prevent the user from simply re-provisioning and obtaining a new certificate. To re-provision the device, the revoked certificate must be deleted. If the device is provisioned with an EAP-TLS client certificate, revoking the certificate will cause the certificate authority to update the certificate's state. When the certificate is next used for authentication, it will be recognized as a revoked certificate and the device will be denied access. NOTE: When using EAP-TLS authentication, you must configure your authentication server to use either OCSP or CRL to check the revocation status of a client certificate. OCSP is recommended as it offers a real-time status update for certificates. If the device is provisioned with PEAP unique device credentials, revoking the certificate will automatically delete the unique username and password associated with the device. When this username is next used for authentication, it will not be recognized as valid and the device will be denied access. NOTE: OCSP and CRL are not used when using PEAP unique device credentials. The ClearPass Onbord server automatically updates the status of the username when the device's client certificate is revoked. 70 | Certificate Configuration in a Cluster Dell Networking W-ClearPass Guest 6.0 | Deployment Guide