Dell Powerconnect W-ClearPass Virtual Appliances W-ClearPass Guest 6.0 Deploym - Page 72
Configuring Online Certificate Status Protocol, Configuring Certificate Revocation List (CRL)
 |
View all Dell Powerconnect W-ClearPass Virtual Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 72 highlights
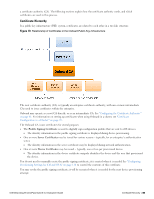
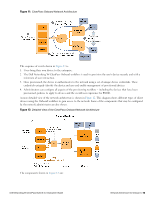
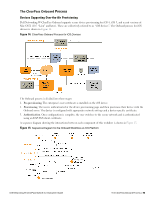
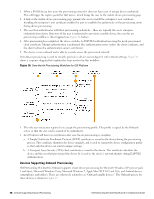
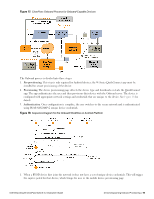
l Configure the provisioning SSID to use PEAP, or another suitable authentication method. l When a user connects to the provisioning SSID, place them into a provisioning role. n The provisioning role should have limited network access and a captive portal that redirects users to the device provisioning page. l When a user connects to the provisioned SSID, authenticate based on the type of credentials presented. n For PEAP authentication with unique device credentials, place them into a provisioned role. n For EAP-TLS authentication using an Onboard client certificate, place them into the provisioned role. n In all other cases, deny access. As for the single-SSID case, additional authorization steps may be taken after authentication has completed to determine the appropriate provisioned role. Configuring Online Certificate Status Protocol Onboard supports the Online Certificate Status Protocol (OCSP) to provide a real-time check on the validity of a certificate. To configure OCSP for your network, you will need to provide the URL of an OCSP service to your network equipment. This URL can be constructed by using the relative path mdps_ocsp.php/1. For example, if the Onboard server's hostname is onboard.example.com, the OCSP URL to use is: http://onboard.example.com/mdps_ocsp.php/1. NOTE: OCSP does not require the use of HTTPS and can be configured to use HTTP. Configuring Certificate Revocation List (CRL) Onboard supports generating a Certificate Revocation List (CRL) that lists the serial numbers of certificates that have been revoked. To configure a CRL, you will need to provide its URL to your network equipment. This URL can be constructed by using the relative path mdps_crl.php?id=1. For example, if the Onboard server's hostname is onboard.example.com, the location of the CRL is: http://onboard.example.com/mdps_crl.php?id=1. NOTE: A certificate revocation list does not require the use of HTTPS and can be configured to use HTTP. Network Architecture for Onboard The high-level network architecture for the Onboard solution is shown in the following figure. 72 | Configuring Online Certificate Status Protocol Dell Networking W-ClearPass Guest 6.0 | Deployment Guide