Dell Powerconnect W-ClearPass Virtual Appliances W-ClearPass Guest 6.0 Deploym - Page 74
Network Architecture for Onboard when Using ClearPass Guest,
 |
View all Dell Powerconnect W-ClearPass Virtual Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 74 highlights
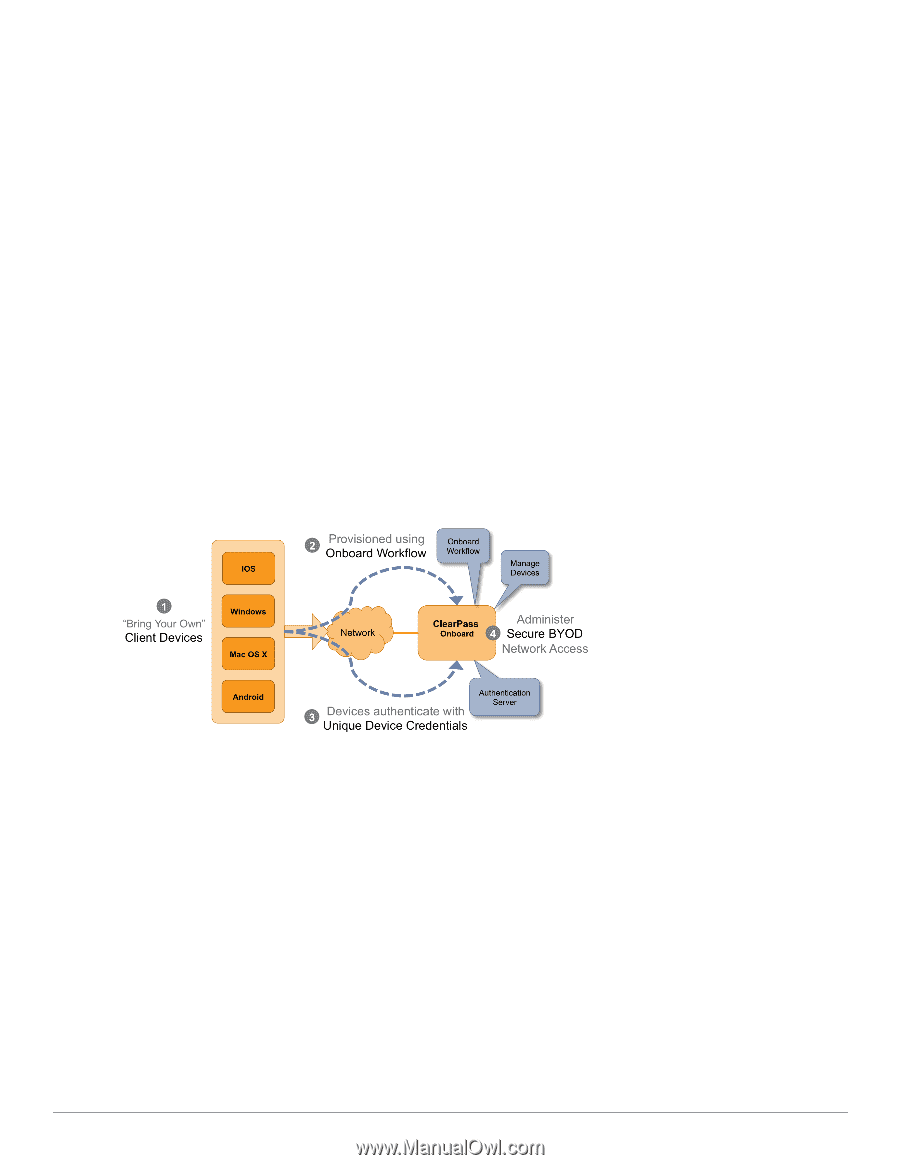
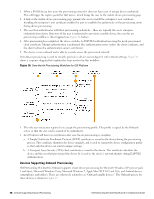
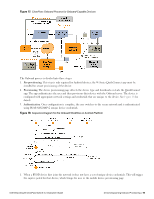
1. Users bring different kinds of client device with them. Onboard supports "smart devices" that use the iOS or Android operating systems, such as smartphones and personal tablets. Onboard also supports the most common versions of Windows and Mac OS X operating systems found on desktop computers, laptops and netbooks. 2. The Onboard workflow is used to provision the user's device securely and with a minimum of user interaction. The provisioning method used depends on the type of device. a. Newer versions of Mac OS X (10.7 and later) and iOS devices use the "over-the-air" provisioning method. b. Other supported platforms use the "Onboard provisioning" method. 3. Once provisioned, client devices use a secure authentication method based on 802.1X and the capabilities best supported by the device. a. The unique device credentials issued during provisioning are in the form of an EAP-TLS client certificate for iOS devices and OS X (10.7+) devices. b. Other supported devices are also issued a client certificate, but will use the PEAP-MSCHAPv2 authentication method with a unique username and strong password. 4. Administrators can manage all Onboard devices using the certificate issued to that device. Network Architecture for Onboard when Using ClearPass Guest ClearPass Guest supports the provisioning, authentication, and management aspects of the complete Onboard solution. Figure 13 shows the high-level network architecture for the Onboard solution when using ClearPass Guest as the provisioning and authentication server. Figure 13: ClearPass Onboard Network Architecture when Using ClearPass Guest The user experience for device provisioning is the same in Figure 13 and Figure 11, however there are implementation differences between these approaches: l When using the ClearPass Guest RADIUS server for provisioning and authentication, EAP-TLS and PEAP authentication must be configured. Navigate to RADIUS > Authentication > EAP & 802.1X to configure a server certificate and the appropriate EAP types for the ClearPass Guest RADIUS server. l ClearPass Policy Manager supports a rich policy definition framework. If you have complex policies to enforce, multiple authentication or authorization sources that define user accounts, or you need features beyond those available in the ClearPass Guest RADIUS server, you should deploy Policy Manager for authentication. 74 | Network Architecture for Onboard when Using ClearPass Guest Dell Networking W-ClearPass Guest 6.0 | Deployment Guide