Dell Powerconnect W-ClearPass Virtual Appliances W-ClearPass Guest 6.0 Deploym - Page 85
Email Address, Organizational Unit
 |
View all Dell Powerconnect W-ClearPass Virtual Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 85 highlights
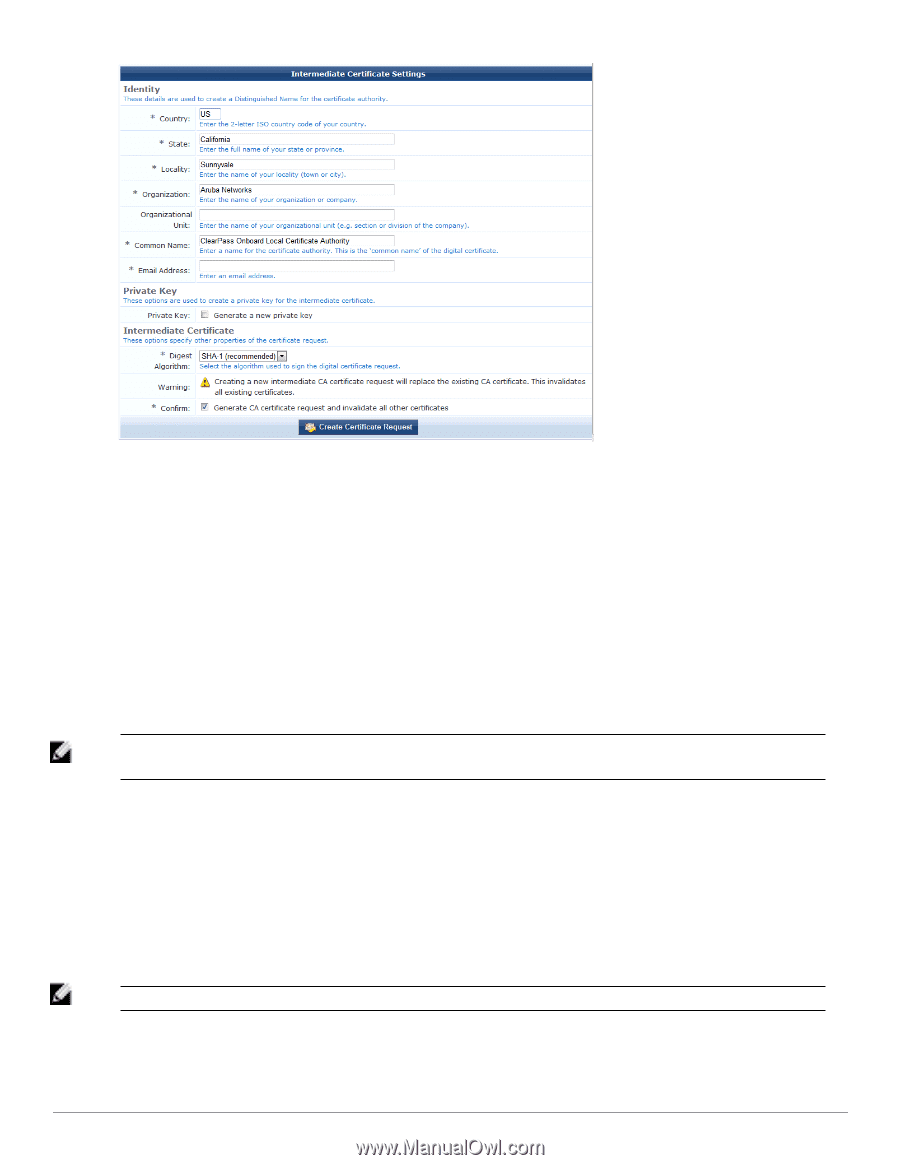
In the Identity section of the form: l Enter values in the Country, State, Locality, Organization, and Organizational Unit text fields that correspond to your organization. These values form part of the distinguished name for the certificate authority. l Enter a descriptive name for the certificate authority in the Common Name text field. This value will be used to identify the intermediate certificate as the issuer of client and server certificates from this certificate authority. l Enter a contact email address in the Email Address text field. This email address will be included in the certificate authority's certificate, and provides a way for users of the certificate authority to contact your organization. In the Private Key section: l To create a new private key for the intermediate certificate, mark the Generate a new private key check box. The form expands to include the Key Type drop-down list. Creating a new key is only necessary if you are recreating the entire certificate authority from the beginning. NOTE: If you have previously created any client or server certificates or performed device provisioning using the existing intermediate CA certificate, these certificates will be invalidated when changing the intermediate CA's private key. l The Key Type drop-down list specifies the type of private key that should be created for the certificate. You can select one of these options: n 1024-bit RSA - not recommended for a certificate authority n 2048-bit RSA - recommended for general use n 4096-bit RSA - higher security In the Intermediate Certificate section: l The Digest Algorithm drop-down list allows you to specify which hash algorithm should be used. NOTE: MD5 is not recommended for use with certificate authority certificates. Mark the Generate CA certificate request and invalidate all other certificates check box to confirm the changes. Dell Networking W-ClearPass Guest 6.0 | Deployment Guide Setting Up an Intermediate Certificate Authority | 85