Dell Powerconnect W-ClearPass Virtual Appliances W-ClearPass Guest 6.0 Deploym - Page 69
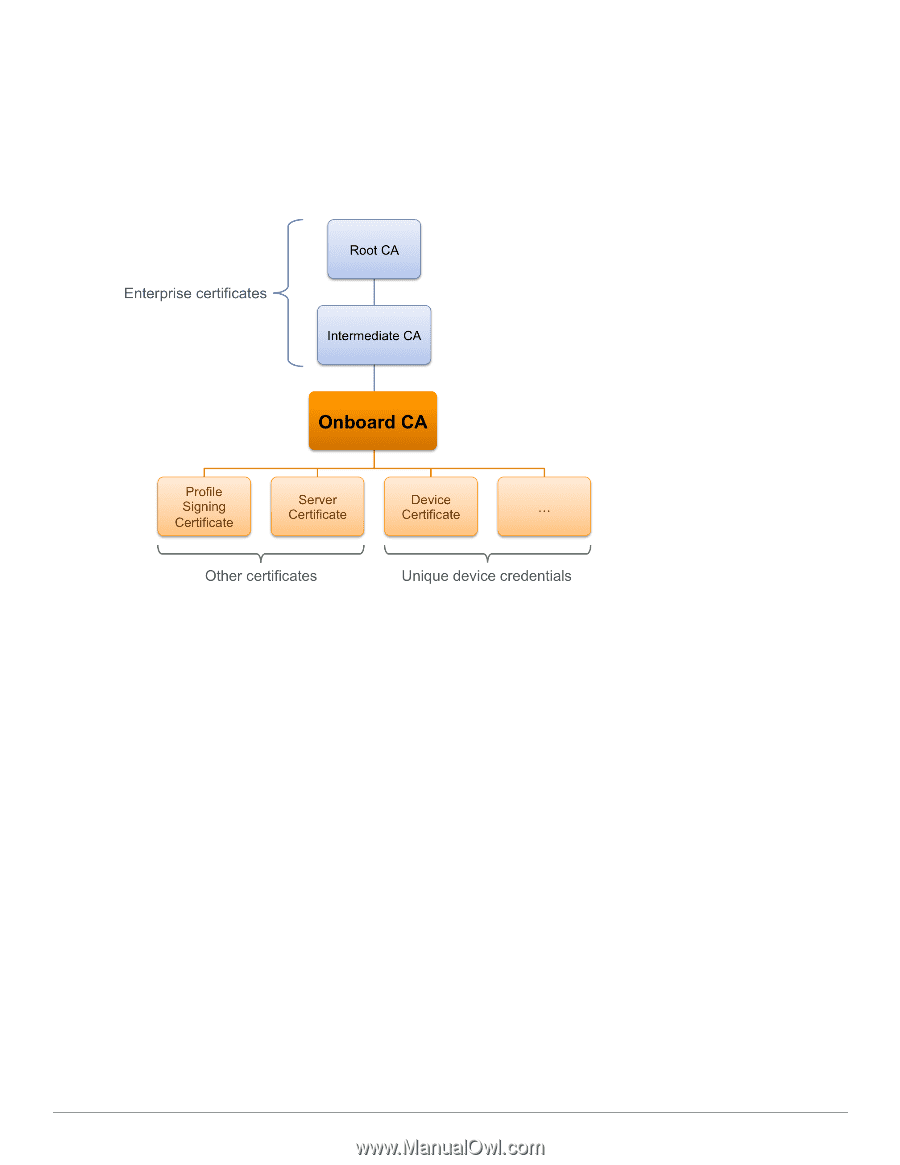
Certificate Hierarchy,
 |
View all Dell Powerconnect W-ClearPass Virtual Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 69 highlights
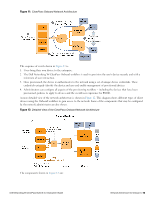
a certificate authority (CA). The following sections explain how the certificate authority works, and which certificates are used in this process. Certificate Hierarchy In a public key infrastructure (PKI) system, certificates are related to each other in a tree-like structure. Figure 10: Relationship of Certificates in the Onboard Public Key Infrastructure The root certificate authority (CA) is typically an enterprise certificate authority, with one or more intermediate CAs used to issue certificates within the enterprise. Onboard may operate as a root CA directly, or as an intermediate CA. See "Configuring the Certificate Authority " on page 81. For information on setting up certificates when using Onboard in a cluster, see "Certificate Configuration in a Cluster " on page 70. The Onboard CA issues certificates for several purposes: l The Profile Signing Certificate is used to digitally sign configuration profiles that are sent to iOS devices. n The identity information in the profile signing certificate is displayed during device provisioning. l One or more Server Certificates may be issued for various reasons - typically, for an enterprise's authentication server. n The identity information in the server certificate may be displayed during network authentication. l One or more Device Certificates may be issued - typically, one or two per provisioned device. n The identity information in the device certificate uniquely identifies the device and the user that provisioned the device. You do not need to manually create the profile signing certificate; it is created when it is needed See "Configuring Provisioning Settings for iOS and OS X" on page 110 to control the contents of this certificate. You may revoke the profile signing certificate; it will be recreated when it is needed for the next device provisioning attempt. Dell Networking W-ClearPass Guest 6.0 | Deployment Guide Certificate Hierarchy | 69