HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.1.x administrator guide (5697 - Page 126
IP Filter policy enforcement
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 126 highlights
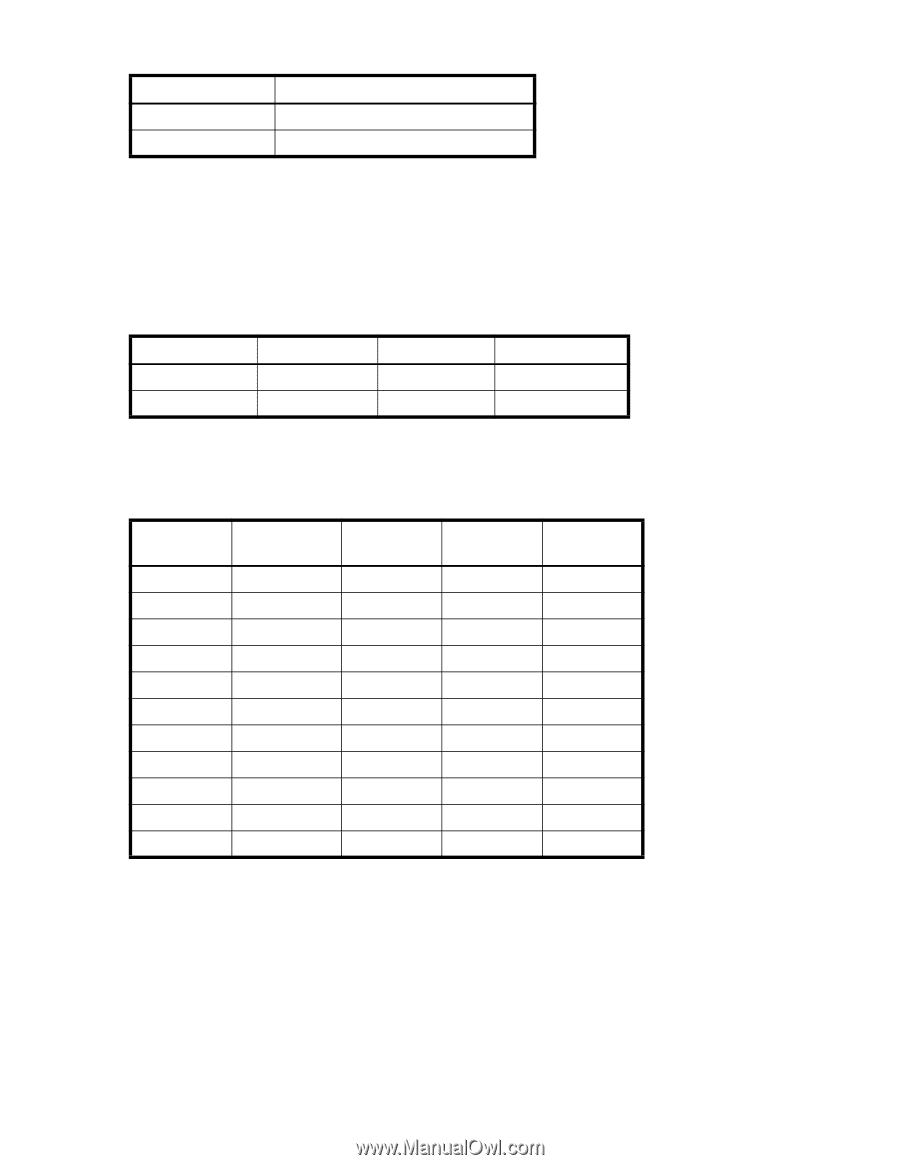
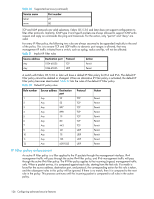
Table 30 Supported services (continued) Service name Port number telnet 23 www 80 TCP and UDP protocols are valid selections. Fabric OS 5.3.0 and later does not support configuration to filter other protocols. Implicitly, ICMP type 0 and type 8 packets are always allowed to support ICMP echo request and reply on commands like ping and traceroute. For the action, only "permit" and "deny" are valid. For every IP Filter policy, the following two rules are always assumed to be appended implicitly to the end of the policy. This is to ensure TCP and UDP traffics to dynamic port ranges is allowed, that way management IP traffic initiated from a switch, such as syslog, radius and ftp, will not be affected. Table 31 Implicit IP Filter rules Source address Destination port Protocol Action Any 1024-65535 TCP Permit Any 1024-65535 UDP Permit A switch with Fabric OS 5.3.0 or later will have a default IP Filter policy for IPv4 and IPv6. The default IP Filter policy cannot be deleted or changed. When an alternative IP Filter policy is activated, the default IP Filter policy becomes deactivated. Table 32 lists the rules of the default IP Filter policy. Table 32 Default IP policy rules Rule number Source address Destination port Protocol Action 1 Any 22 TCP Permit 2 Any 23 TCP Permit 3 Any 897 TCP Permit 4 Any 898 TCP Permit 5 Any 111 TCP Permit 6 Any 80 TCP Permit 7 Any 443 TCP Permit 9 Any 161 UDP Permit 10 Any 111 UDP Permit 11 Any 123 UDP Permit 12 Any 600-1023 UDP Permit IP Filter policy enforcement An active IP Filter policy is a filter applied to the IP packets through the management interface. IPv4 management traffic will pass through the active IPv4 filter policy, and IPv6 management traffic will pass through the active IPv6 filter policy. The IP Filter policy applies to the incoming (ingress) management traffic only. When a packet arrives, it is compared against each rule, starting from the first rule. If a match is found for the source address, destination port, and protocol, the corresponding action for this rule is taken, and the subsequent rules in this policy will be ignored. If there is no match, then it is compared to the next rule in the policy. This process continues until the incoming packet is compared to all rules in the active policy. 126 Configuring advanced security features