HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.1.x administrator guide (5697 - Page 127
Creating IP Filter policy rules, Deleting IP Filter policy rules, Switch session transactions
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 127 highlights
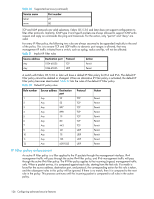
If none of the rules in the policy matches the incoming packet, the two implicit rules will be matched to the incoming packet. If the rules still do not match the packet, the default action, which is to deny, will be taken. When the IPv4 or IPv6 address for the management interface of a switch is changed through the ipAddrSet command or manageability tools, the active IP Filter policies will automatically become enforced on the management IP interface with the changed IP address. NOTE: If a switch is part of a LAN behind a Network Address Translation (NAT) server, depending on the NAT server configuration, the source address in an IP Filter rule may have to be the NAT server address. Creating IP Filter policy rules There can be a maximum of 256 rules created for an IP Filter policy. The change to the specified IP Filter policy is not saved to the persistent configuration until a save or activate sub-command is run. To add a rule to an IP Filter policy: 1. Log in to the switch using an account assigned to the admin role. 2. Type in the following command: ipfilter --addrule -rule -sip -dp -proto -act policyname Specifies the policy name which is a unique string composed of a maximum of 20 alphanumeric and underscore characters. The names default_ipv4 and default_ipv6 are reserved for the default IP Filter policies. The policy name is case-insensitive and always stored as lower case. -rule rule number -sip source IP Enter a valid rule number between 1 and the current maximum rule number plus one. Specifies the source IP address. For IPv4 filter type, the address must be a 32-bit address in dot decimal notation, or a CIDR block IPv4 prefix. For IPv6 filter type, the address must be a 128-bit IPv6 address in any format specified by RFC, or a CIDR block IPv6 prefix. -dp destination port -proto protocol -act Deleting IP Filter policy rules Deleting a rule in the specified IP Filter policy causes the rules following the deleted rule to shift up in rule order. The change to the specified IP Filter policy is not saved to persistent configuration until a save or activate sub-command is run. To delete a rule to an IP Filter policy: 1. Log in to the switch using an account assigned to the admin role. 2. Type in the following command: ipfilter --delrule -rule Switch session transactions A transaction is associated with a command line or manageability session. It is opened implicitly when the --create, --addrule, --delrule, --clone, and --delete subcommands are run. The --transabort, --save, or --activate subcommands will explicitly end the transaction owned by the current command line or manageability session. If a transaction is not ended, other command line or manageability sessions are blocked on the sub-commands that would open a new transaction. Fabric OS 6.1.x administrator guide 127